We assume you have already flashed OpenWRT 19.07.0 or newer on your router to follow this tutorial. For this tutorial we used an Asus RT-AC56U router but the steps work on any router running OpenWRT.
Downloading the OpenVPN configuration files
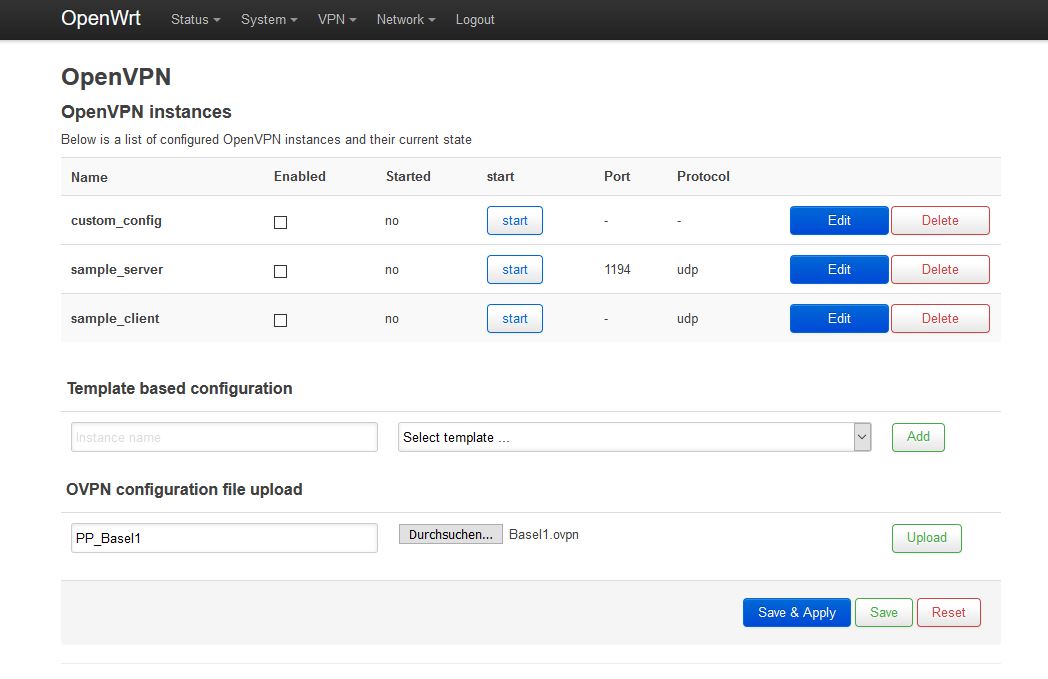
Download the archive with OpenVPN configuration files and unpack it.
Download View alternate downloadsInstall
First download and unpack the archive with the OpenVPN configuration files linked above. Open PuTTY or another terminal program, connect to the router and log in. Successively execute both commands: opkg update and opkg install openvpn-openssl luci-app-openvpn wget sshtunnel sshpass
Download SSH keys
To allow the SSH client to verify it is connected to the appropriate Perfect Privacy VPN server, you first need the known_hosts file containing the public keys of the servers. Download it on OpenWRT using wget: wget https://www.perfect-privacy.com/downloads/perfect_privacy_known_hosts
Adjust configuration
Using WinSCP (of course alternatively the ssh terminal may be used) in the /etc/openvpn/ directory of your OpenWRT router create the file up.sh with the following lines as content
#!/bin/sh
env | sed -n -e "
/^foreign_option_.*=dhcp-option.*DNS/s//nameserver/p
/^foreign_option_.*=dhcp-option.*DOMAIN/s//domain/p
" | sort -u > /tmp/resolv.conf.vpn
uci set dhcp.@dnsmasq[0].resolvfile="/tmp/resolv.conf.vpn"
/etc/init.d/dnsmasq restartand the file down.sh with the following content
#!/bin/sh
uci set dhcp.@dnsmasq[0].resolvfile="/tmp/resolv.conf.auto"
/etc/init.d/dnsmasq restartAnd in the directory /etc/init.d/ teh file pservice with the contents of the this link.
Open the properties of the files up.sh, down.sh and pservice to set the permissions to 755.
Then use PuTTY or another terminal program to execute the following command: /etc/init.d/pservice enable
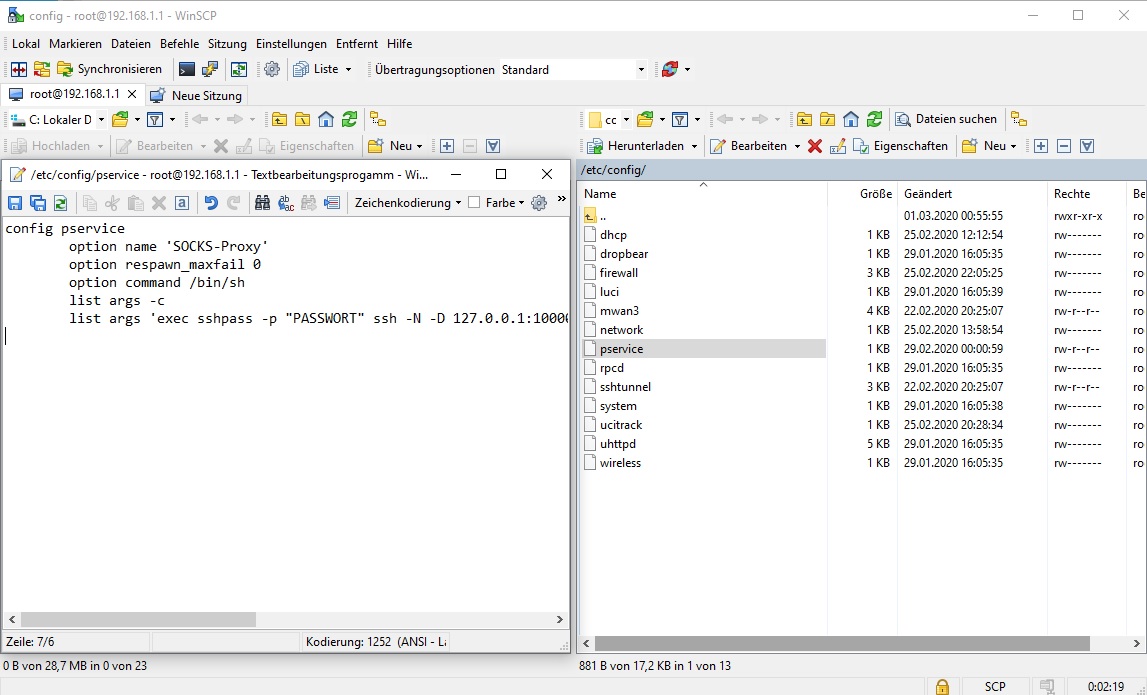
Afterwards create a second pservice file in the directory /etc/config/ with the following content:
config pservice
option name 'OpenVPN-SOCKS-Proxy'
option respawn_maxfail 0
option command /bin/sh
list args -c
list args 'exec sshpass -p "PASSWORD" ssh -N -D 127.0.0.1:10000 -o UserKnownHostsFile=/root/perfect_privacy_known_hosts -p 53 USERNAME@IP_ADDRESS'Instead of IP_ADDRESS enter the IP address of the desired VPN server. These can be found on thr page OpenVPN with Stealth VPN (SSH). Important: Don't use the server's name.
Our recommendation: Choose a location which is geographically close to you, to achieve best possible speed.
Instead of PASSWORD and USERNAME enter your Perfect Privacy credentials.
For the port you can choose between 22, 53, 443, 8085 9009 or 36315. Port 53 and 443 are especially recommendable to circumvent VPN blockings (in this example we decided to use port 53).
DNS server configuration
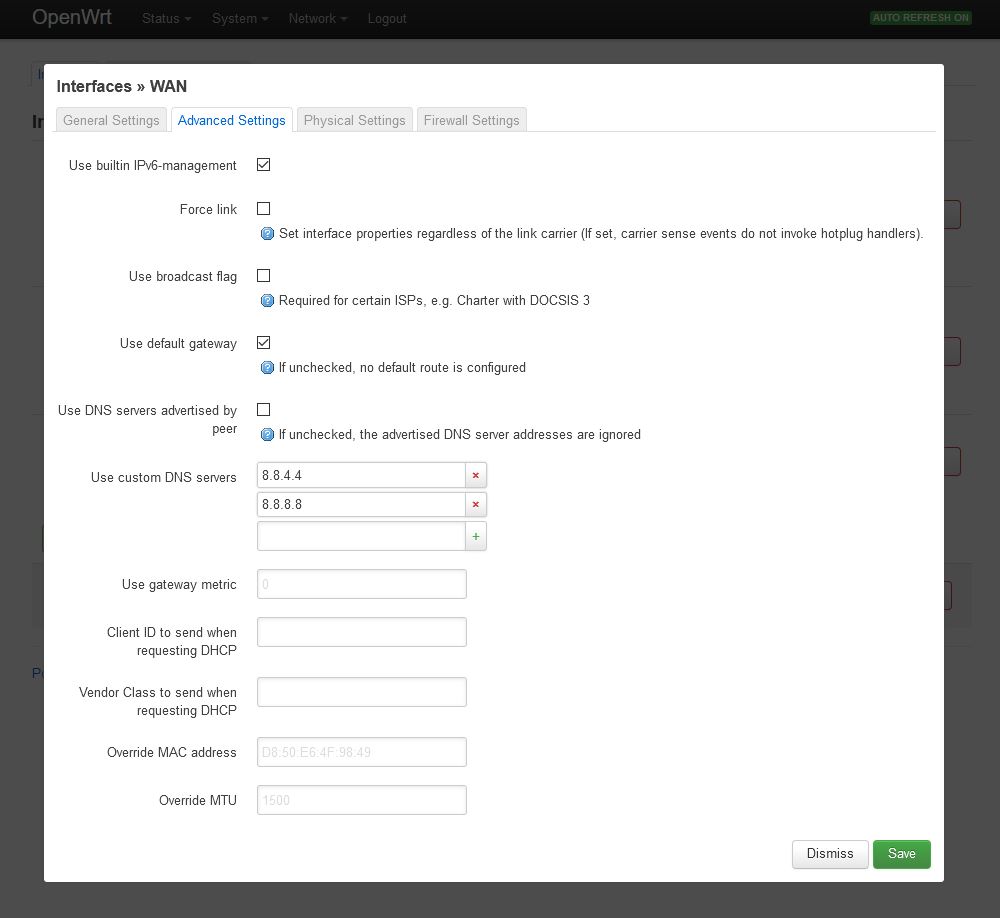
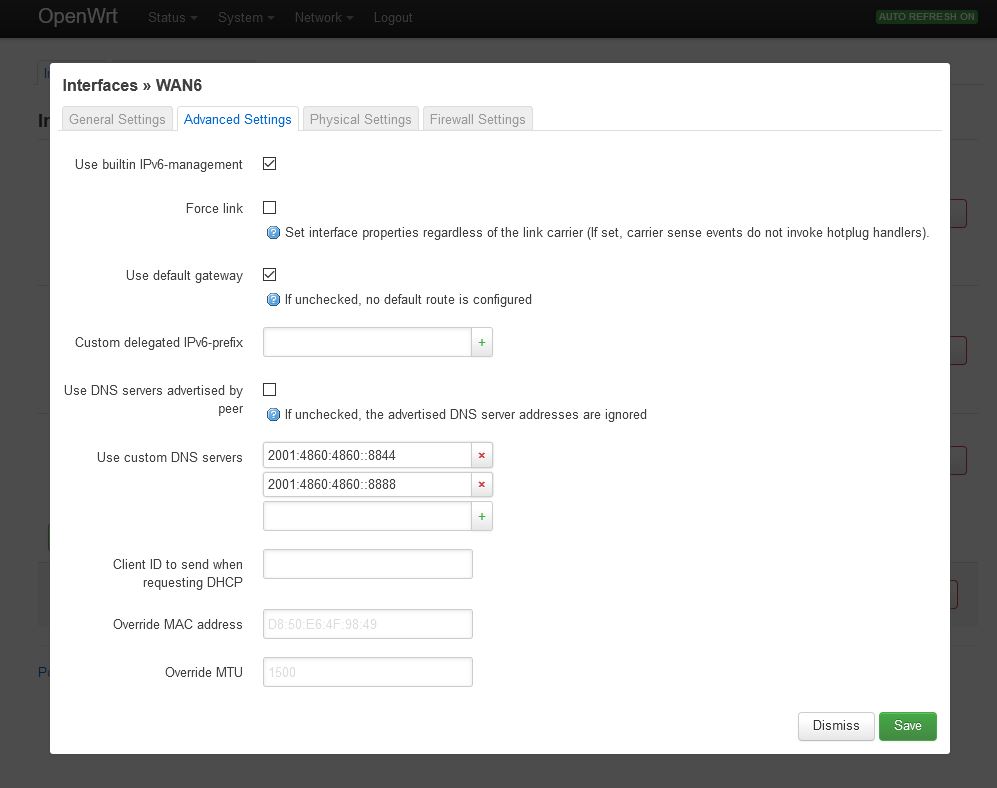
Log in on your OpenWRT router using a web browser (192.168.1.1). Change to the Network=>Interfaces=>WAN=>Edit=>Advanced Settings tab and deactivate Use DNS servers advertised by peer. At Use custom DNS servers enter at least two publicly usable IPv4 DNS servers (e.g. 8.8.8.8 and 8.8.4.4) and click on the Save button.
Do the same in the WAN6 tab and enter at least two IPv6 DNS servers. Then click the Save and the Save & Apply button. You can either use the DNS servers from Google (IPv4: 8.8.8.8 and 8.8.4.4 IPv6: 2001:4860:4860::8888 and 2001:4860:4860::8844) or use some of the OpenNIC project.
Note: If you want, you can also use Perfect Privacy DNS servers (you can find the IPs on the DNS server page in the customer area). These DNS servers will only resolve *.perfect-privacy.com domains when VPN is not connected which means that Internet access will not work without the VPN being connected. However, there will be no IP leak when using public name servers instead, since all DNS requests will be sent anonymized over the VPN tunnel while a VPN connection is established.
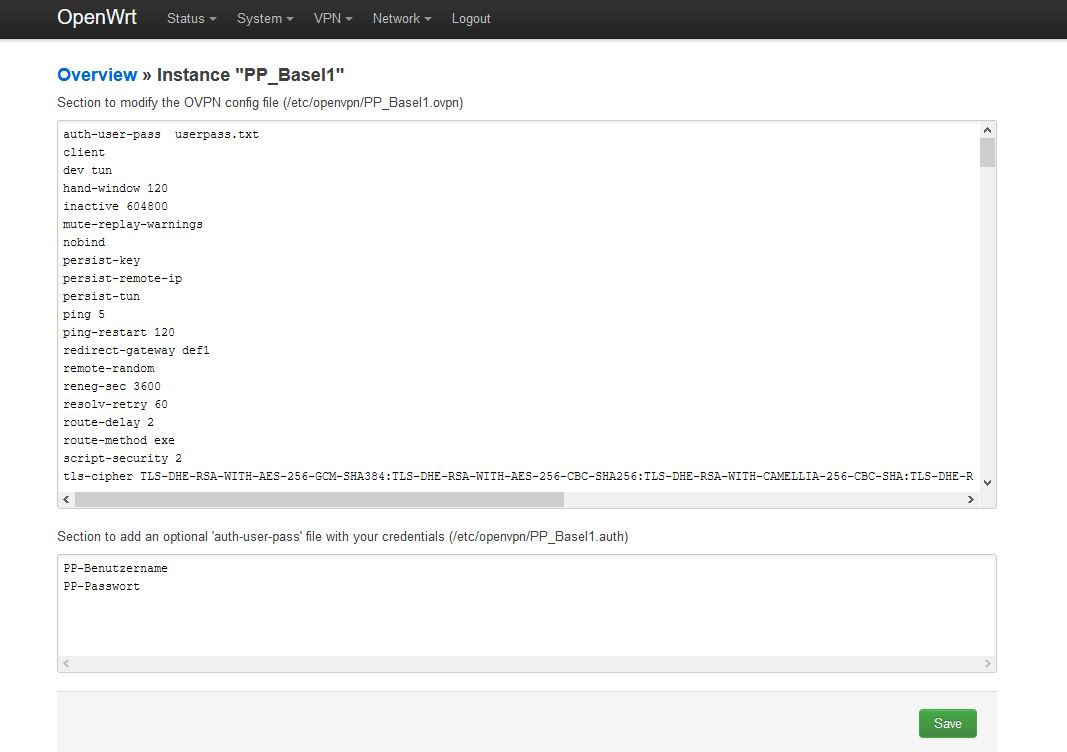
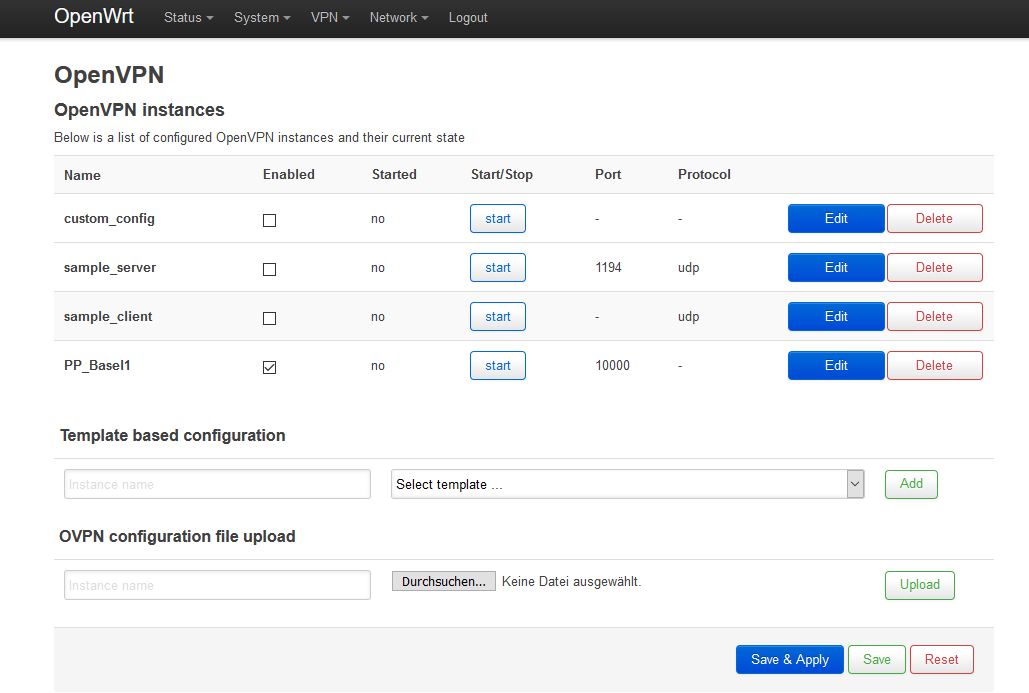
Open the newly created instance PP_Basel1 by clicking Edit and in the first line replace the text "
In the second field fill in your Perfect Privacy username and the corresponding password and then save them by clicking the Save button.
In /var/log/openvpn.log you later may view the log, in case any issues with the OpenVPN connections should occur.
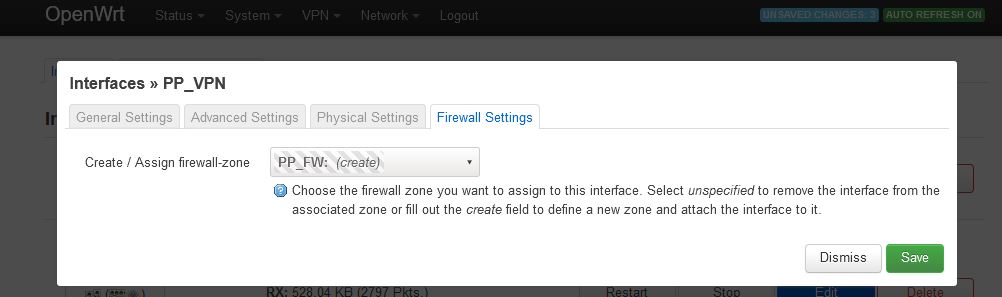
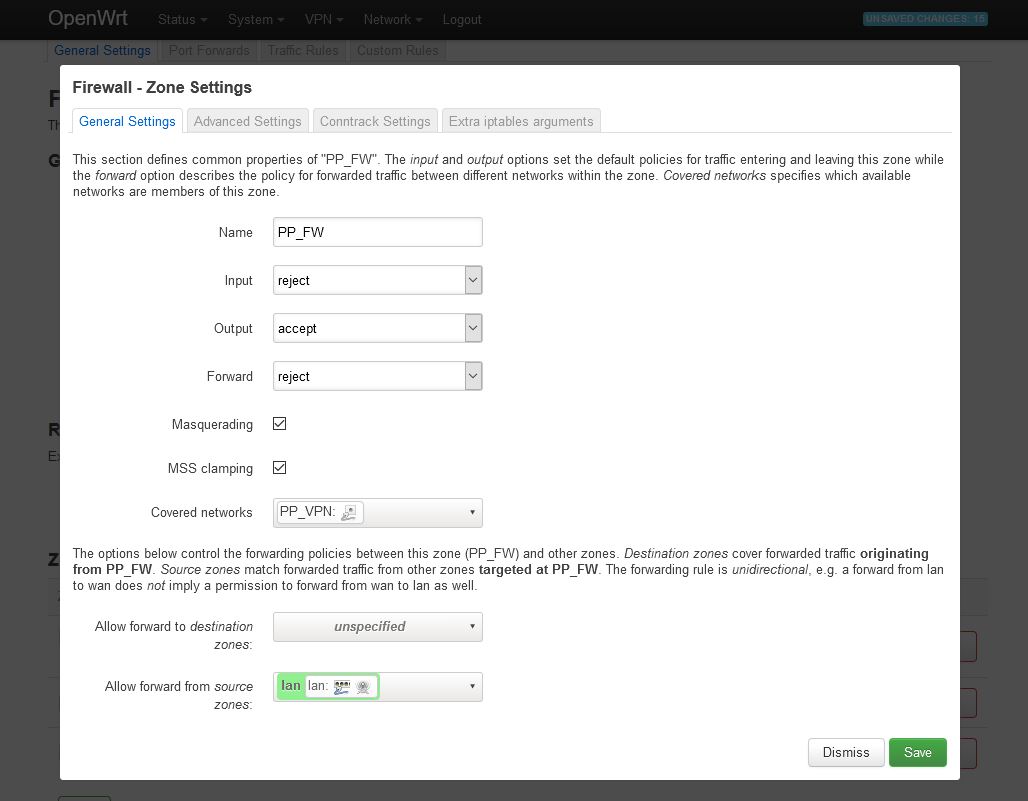
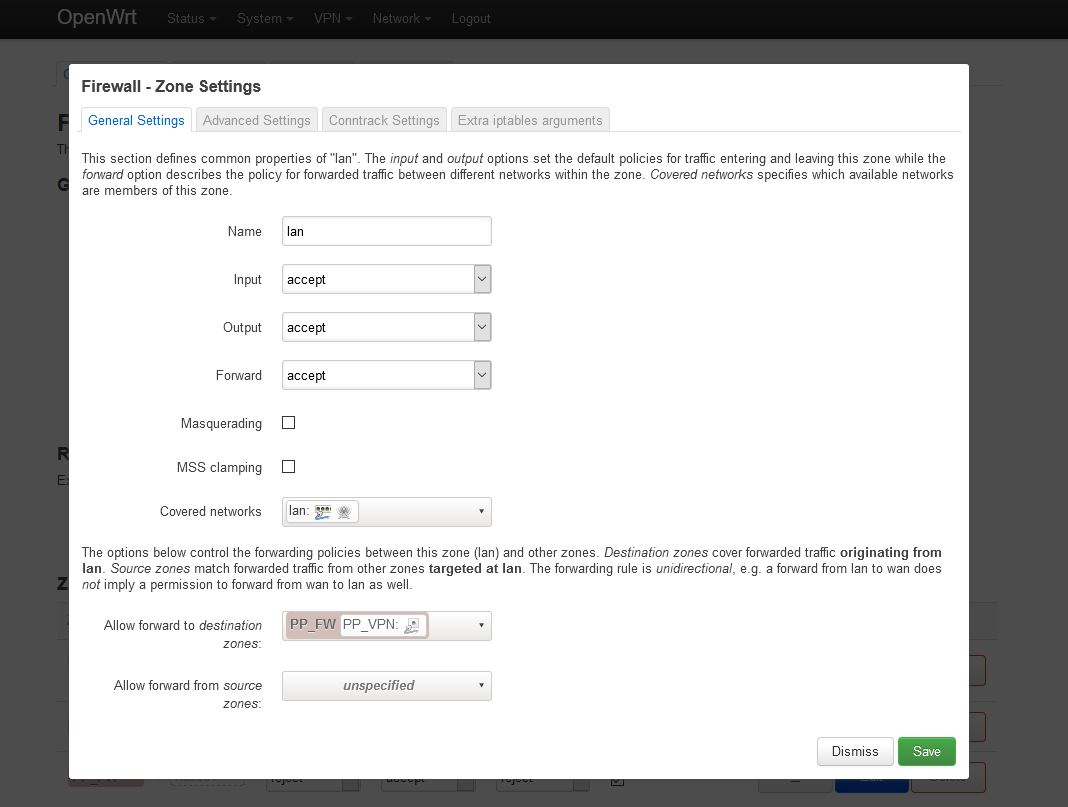
Afterwards navigate to Network=>Firewall and to the right of
- Name:
PP_FW - Input:
reject - Output:
accept - Forward:
reject - Masquerading:
activate - MSS clamping:
activate - Covered networks:
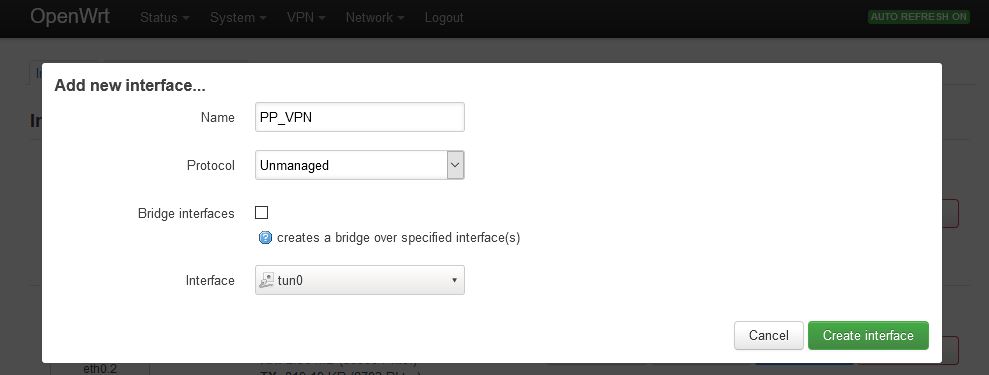
PP_VPN
In the lower field select the following:
- Allow forward from source zones: activate
lan
Use the Save button to accept the settings and then click on Save & Apply.
Optional: Activate the kill-switch
Attention: This step activates the firewall protection ("kill switch"), which ensures in case off an interruption of the internet service no data can bypass the VPN tunnel. If you want to access the internet via your router without VPN too, you have to skip this step.
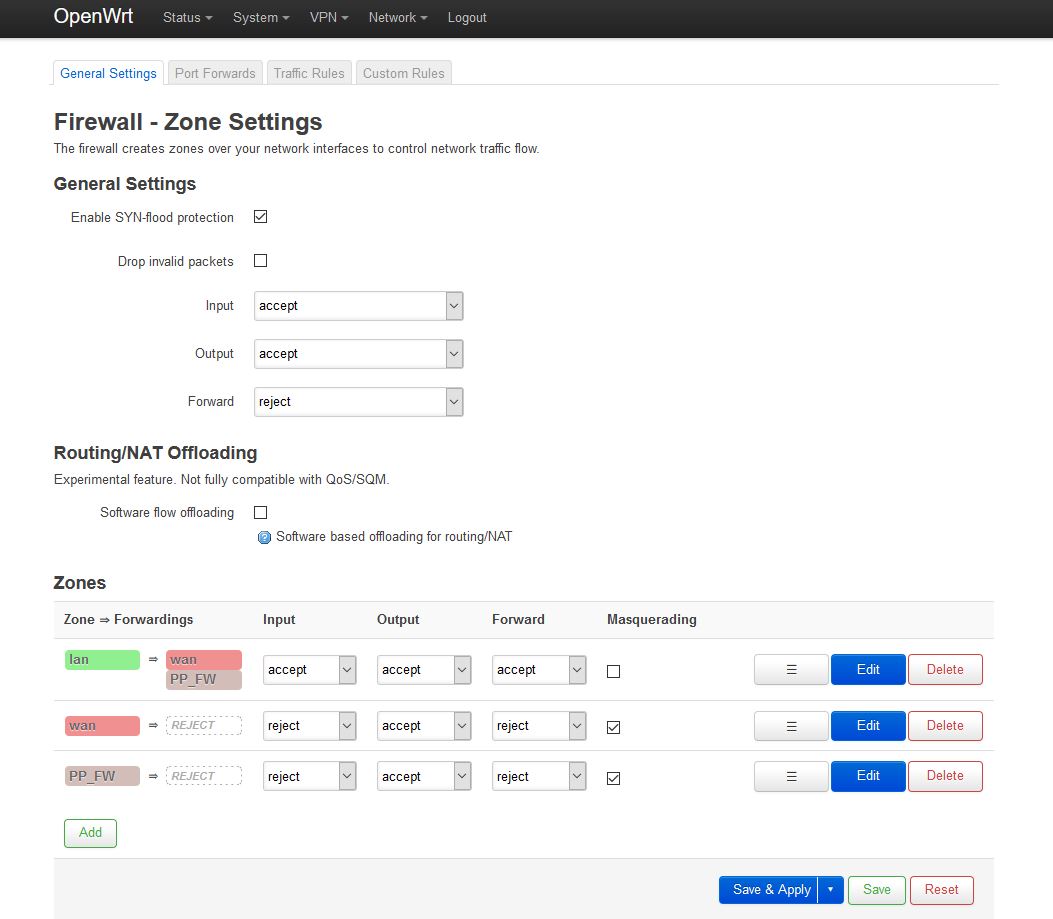
Navigate to Network=>Firewall and underneath Zones open lan using the Edit button.
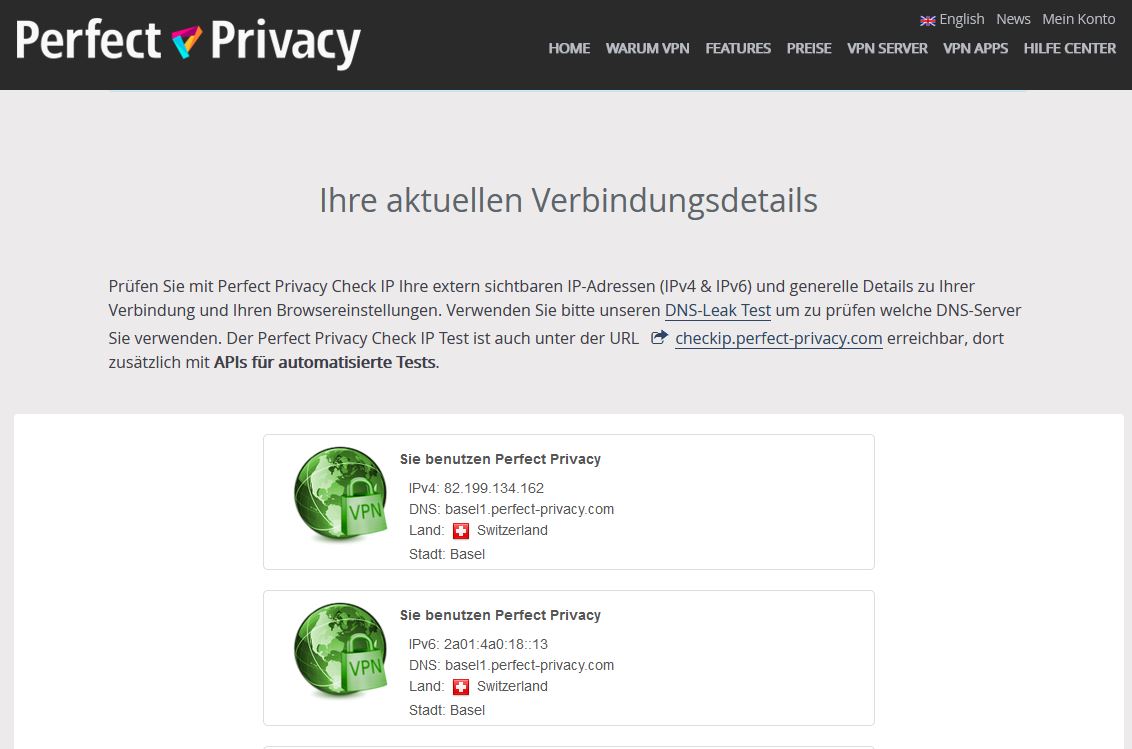
You can verify that the VPN connection is working correctly by visiting our Check-IP website from any device connected to the router.


Questions?
If you have any questions, comments or other feedback regarding this tutorial, please use the corresponding thread in our community forums.