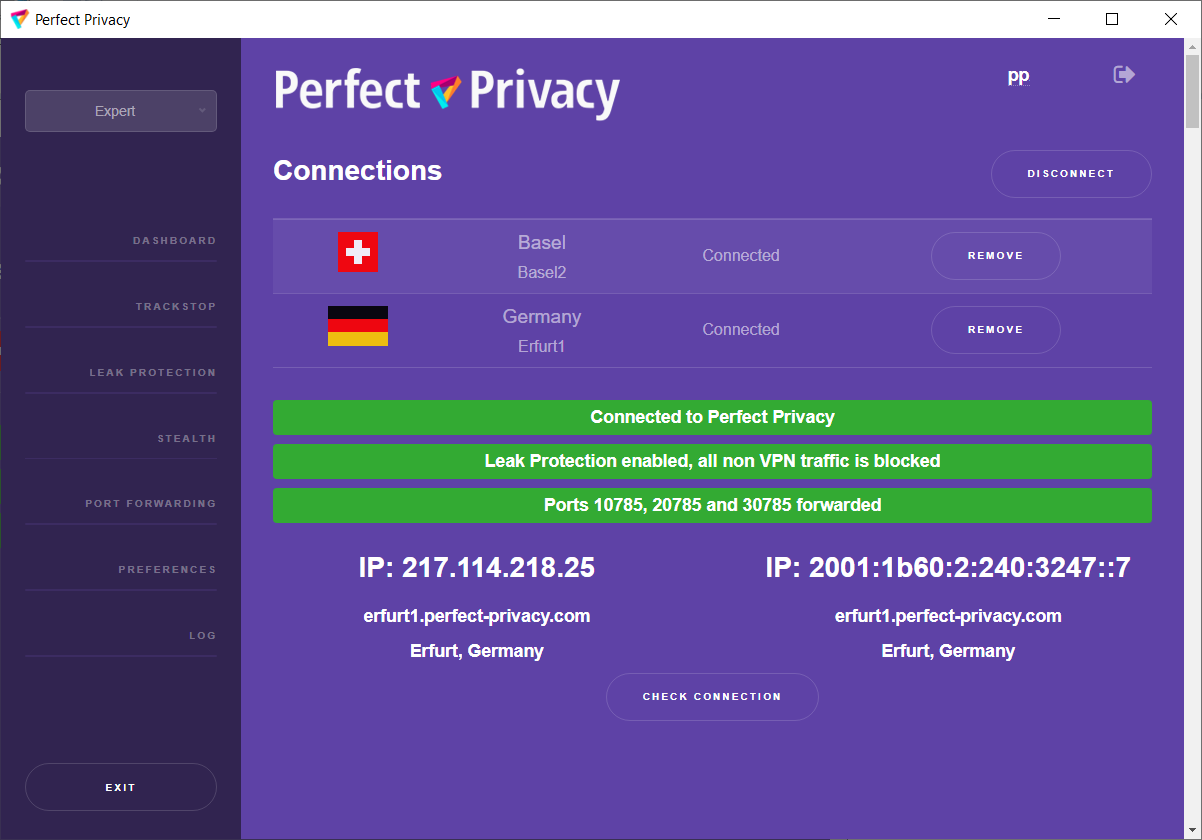
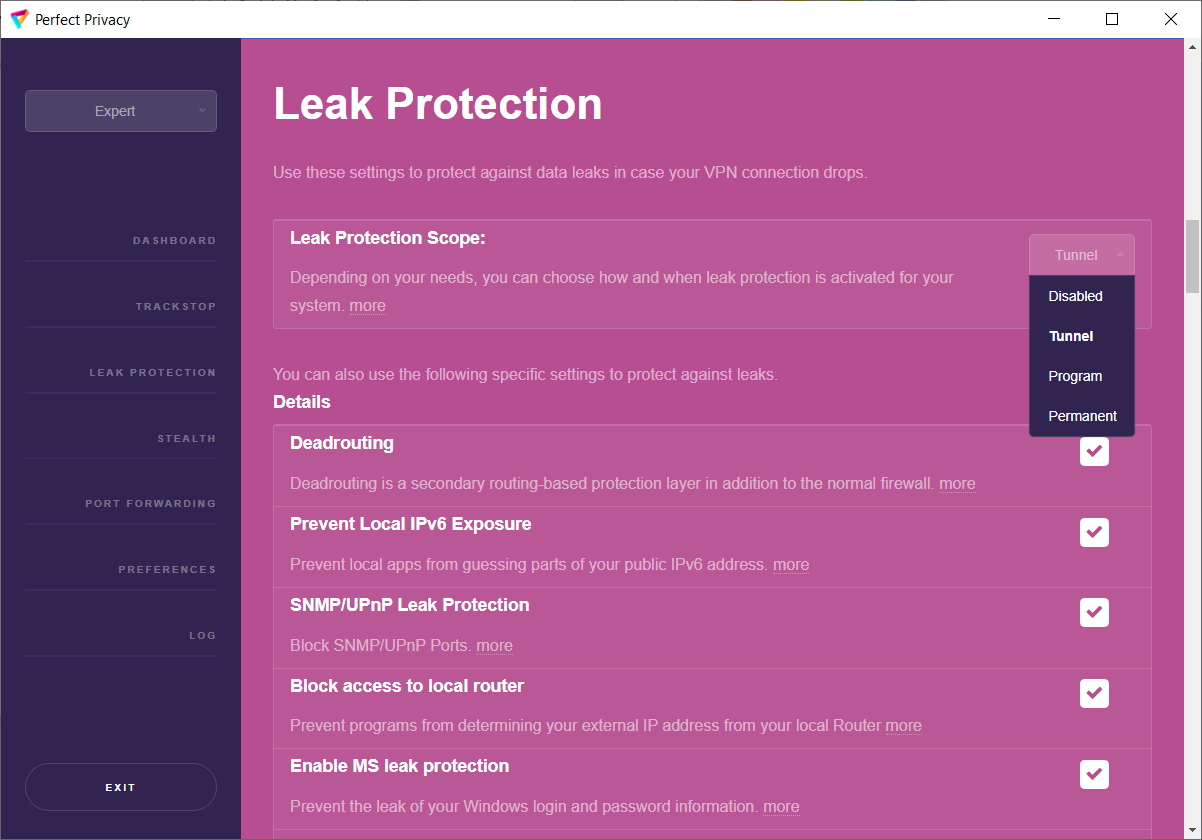
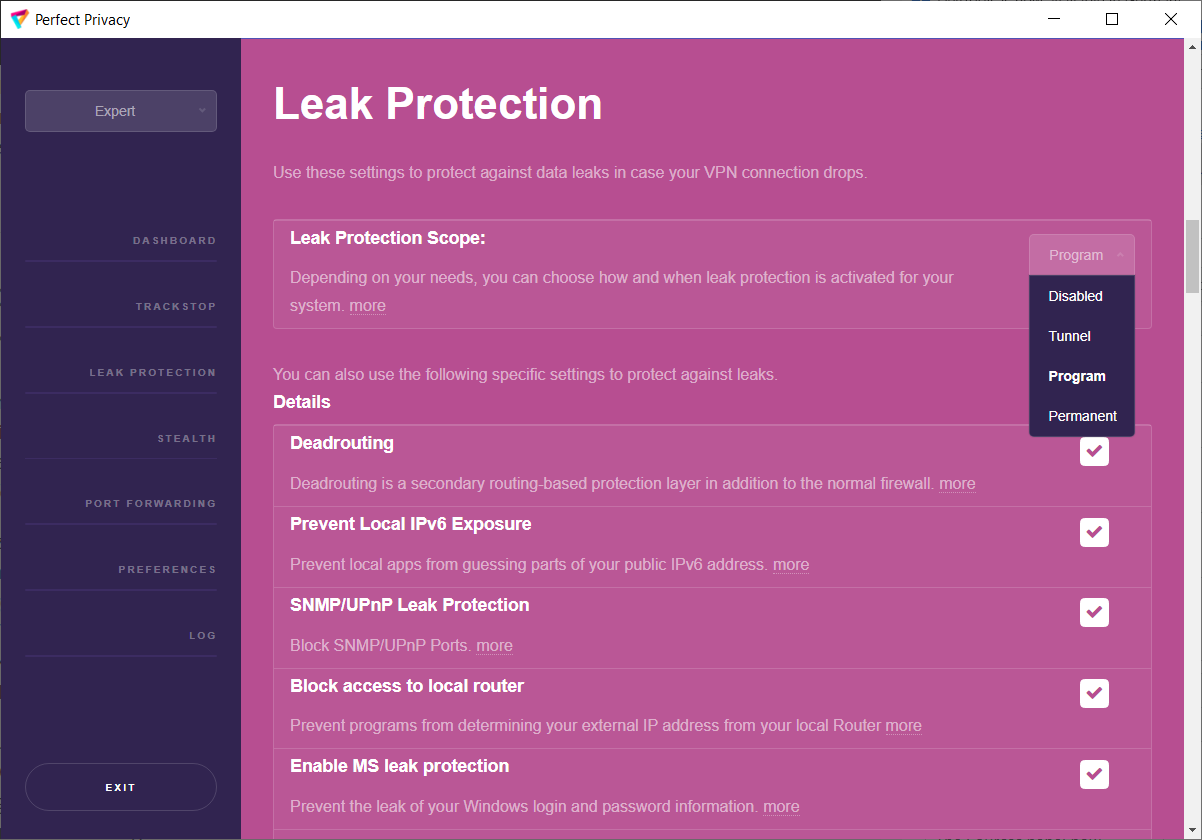
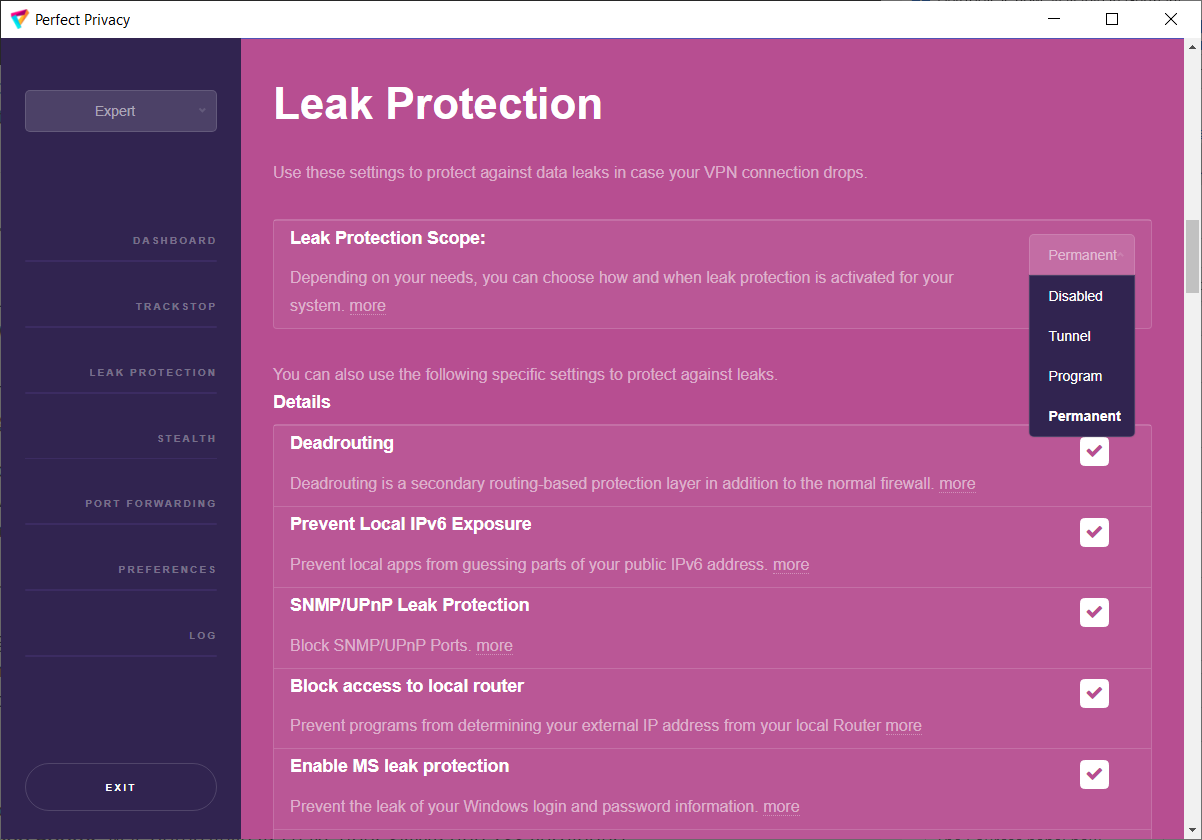
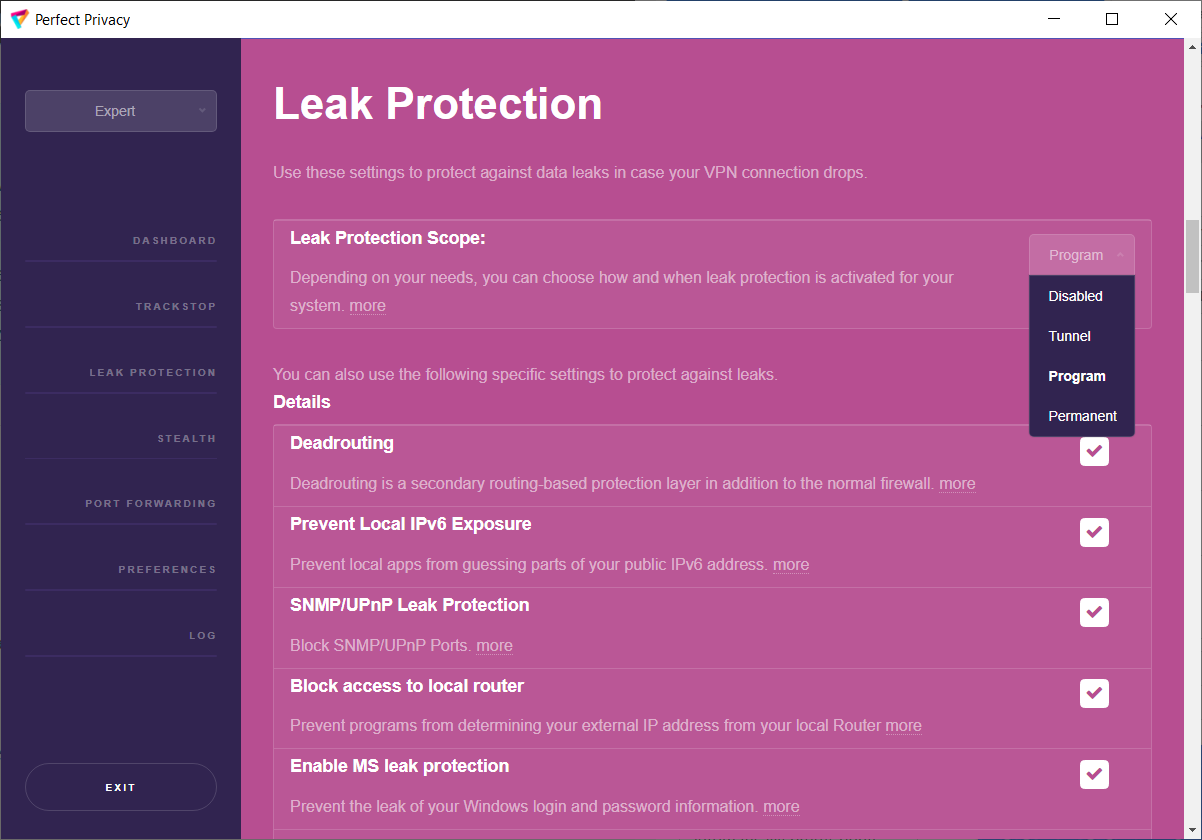
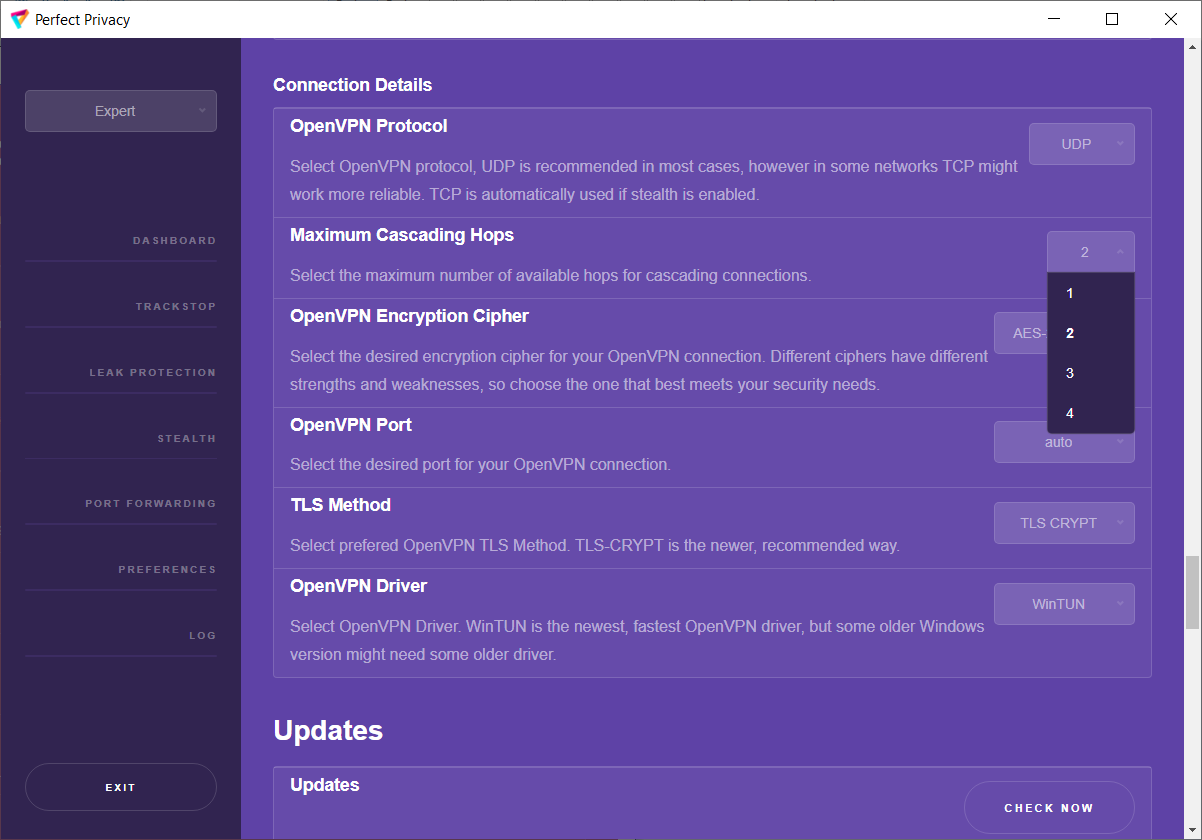
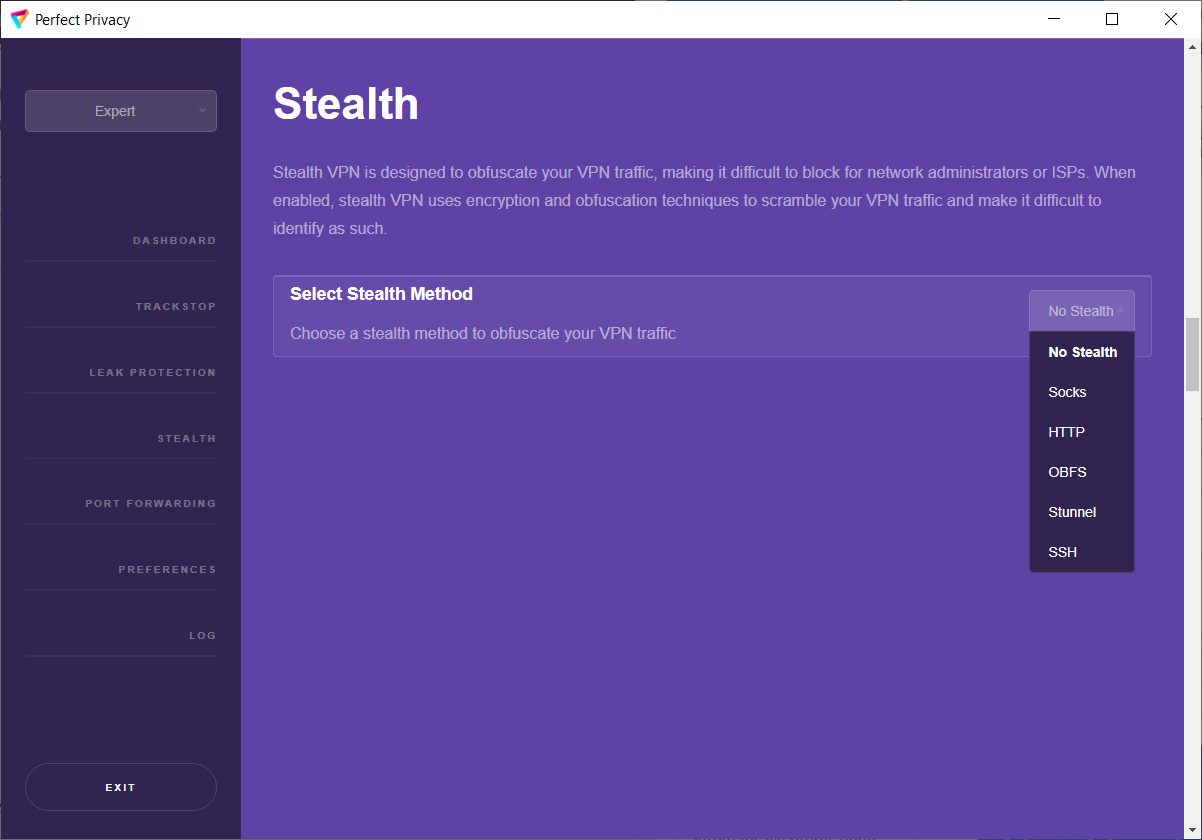
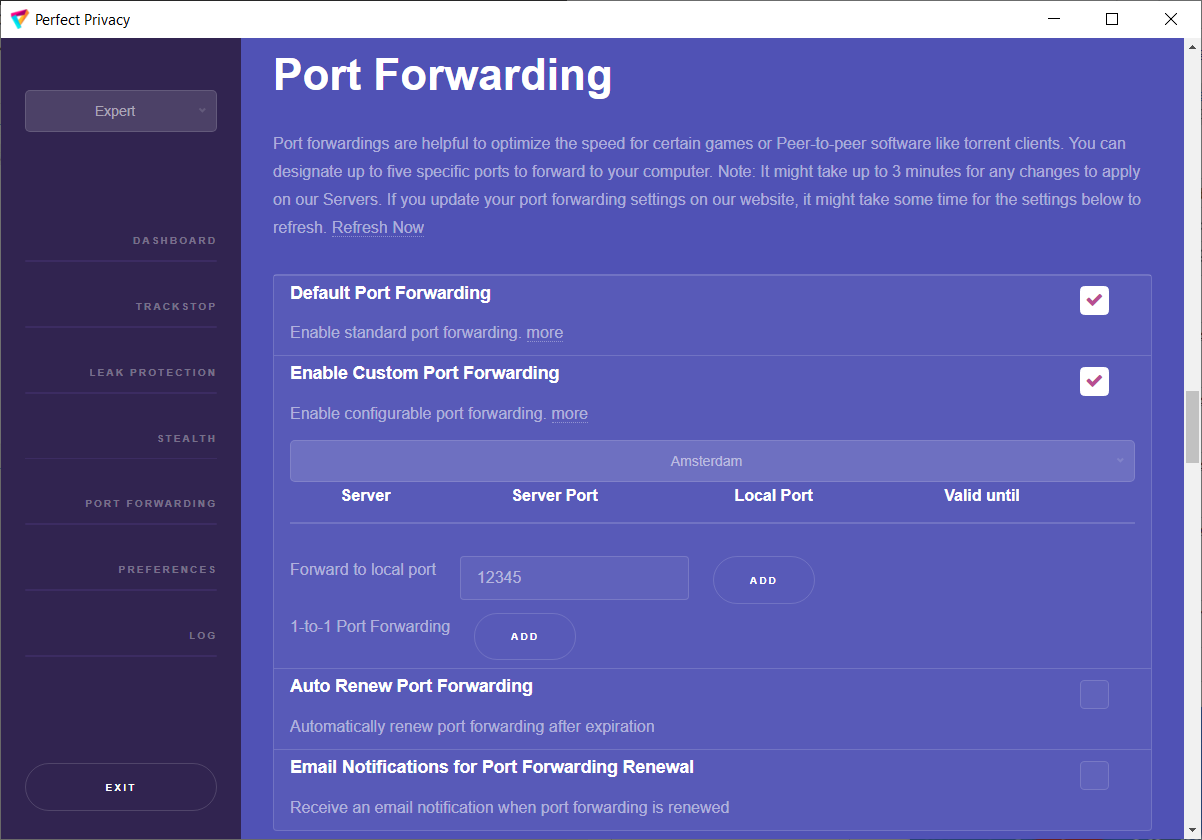
With Perfect Privacy as your VPN provider you have free access to our VPN client software with many advanced features. Our open sourcesoftware, which is developed completely in-house, will automatically update itself and the configuration files so that you can be sure that your software and configuration is always up to date.
The Perfect Privacy VPN Manager for Windows (Vista/7/8/10) offers a lot of additional features that can improve comfort, speed and security. This document explains how to make best use of the functionality of our software. For more detailed information about the settings options in the VPN Manager, click on our documentation .
Software for Linux, macOS, iOS and Android can be found in our download area for apps .