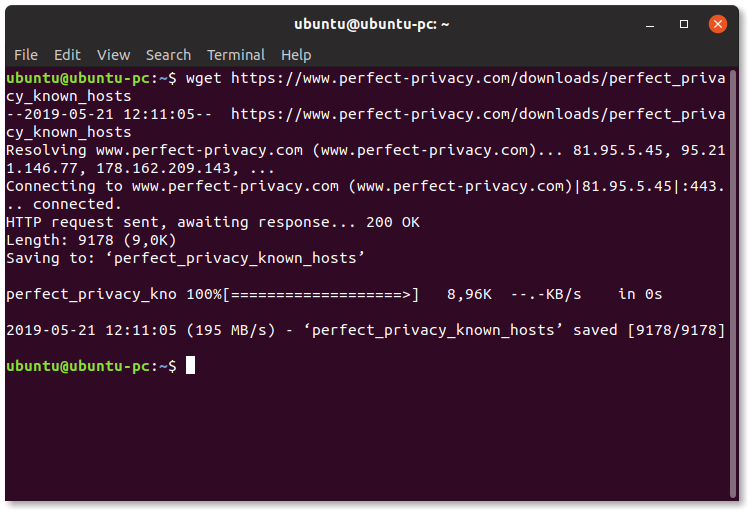
The OpenSSH client is pre-installed on most systems. If this is not the case, please install SSH first:
sudo apt-get install ssh
Starting an encrypted HTTP proxy
The most common use of SSH with Perfect Privacy is for encrypted HTTP proxies. Normally the connection to HTTP proxies is unencrypted, but with SSH this connection can be used encrypted.
Run SSH as follows:
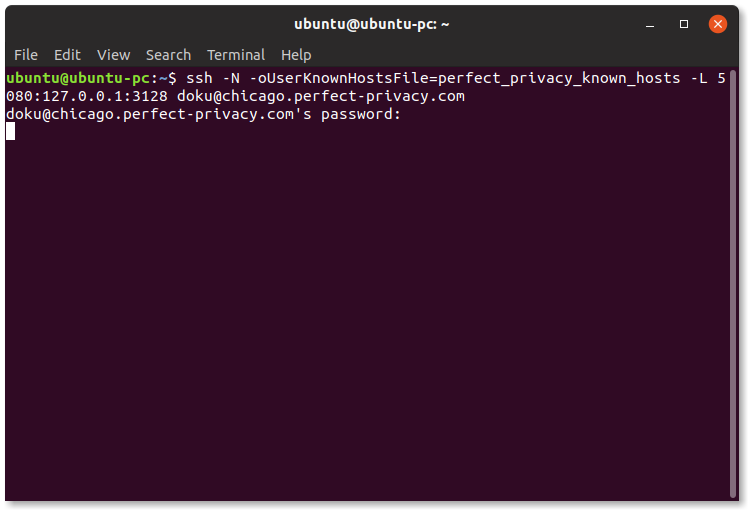
ssh -N -oUserKnownHostsFile=perfect_privacy_known_hosts -L 5080:127.0.0.1:3128 BENUTZERNAME@SERVER
Instead of USERNAME enter your Perfect Privacy username, instead of SERVER enter a server of your choice (in the example frankfurt.perfect-privacy.com).
The number 5080 indicates on which local port the HTTP proxy should be available. Here you can also select any other port.
After entering the Perfect Privacy password, you can use the proxy at 127.0.0.1:5080. The setup of Firefox and Chromium is explained in the SSH Manager manual.
Start an encrypted SOCKS proxy
A SOCKS proxy is very similar to the HTTP proxy in the above points. However, some applications only support one of the two methods.
To do so, start SSH as follows:
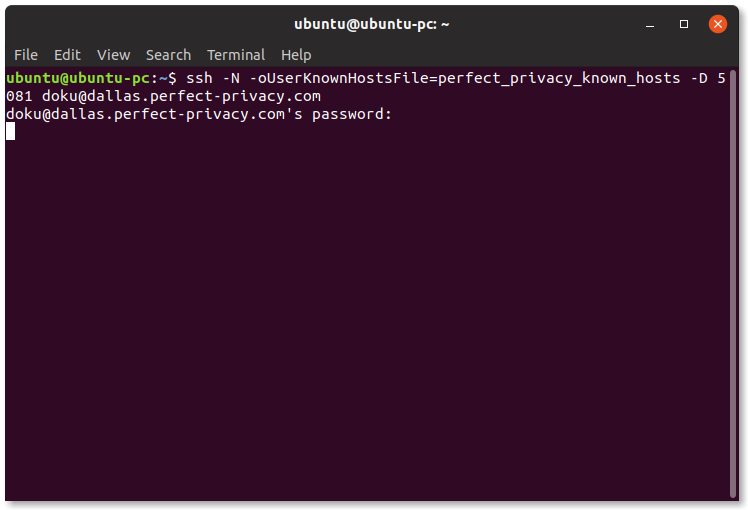
ssh -N -oUserKnownHostsFile=perfect_privacy_known_hosts -D 5081 BENUTZERNAME@SERVER
In this case, 5081 is the port on which the SOCKS proxy is to be available locally.
Tunnelling a Tor proxy over SSH
If you want to get a taste of the Tor network, you can use Perfect Privacy's Tor proxy via SSH. This allows you to access .onion addresses using your normal browser.
To use the Tor proxy, start the SSH connection as follows:
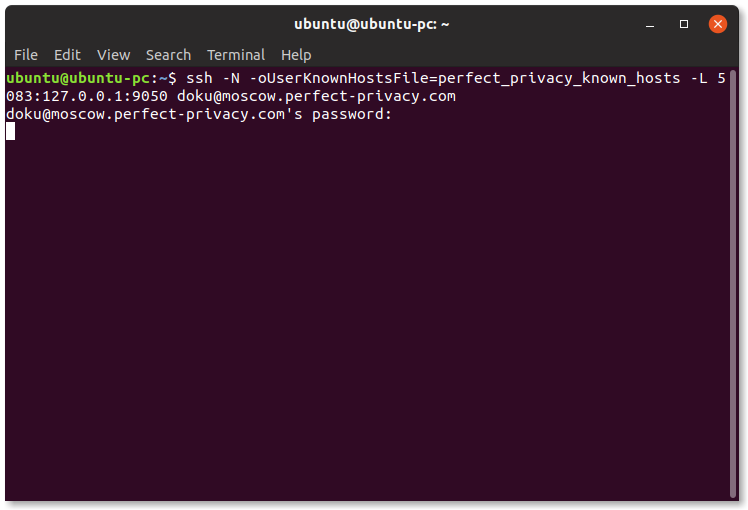
ssh -N -oUserKnownHostsFile=perfect_privacy_known_hosts -L 5083:127.0.0.1:9050 BENUTZERNAME@SERVER
If you are using Tor for security and anonymity reasons, we strongly recommend that you do not use your normal browser and use the Tor Browser Bundle instead.
General port forwarding
The use of SSH with Perfect Privacy is not limited to HTTP, SOCKS and Tor proxies. You can tunnel the connection to any other service through SSH and hide your IP address from service providers.
In this example, we route the connection to the (fictitious) SMTP server mail.example.com on port 25 through the SSH tunnel and make this service available locally on port 5082:
ssh -N -oUserKnownHostsFile=perfect_privacy_known_hosts -L 5082:mail.example.com:25 BENUTZERNAME@SERVER


Questions?
If you have any questions, comments or other feedback regarding this tutorial, please use the corresponding thread in our community forums.