Installation
Open the program PuTTY or any other terminal program and login on the router. Successively execute the following commands: opkg update and opkg install wget sshtunnel sshpass
Downloading the SSH keys
In order to enable the ssh client to check that it has connected to a Perfect Privacy VPN server, you first need the known_hosts file containing the public keys of the servers. Download it on the OpenWRT router using wget: wget https://www.perfect-privacy.com/downloads/perfect_privacy_known_hosts
Information regarding HTTP proxy
The most common usage for SSH at Perfect Privacy is for encrypted access of HTTP proxies. Usually the connection to HTTP proxies is unencrypted, using SSH this connection can be encrypted. The scheme is:
sshpass -p 'PASSWORD' ssh -N -o UserKnownHostsFile=perfect_privacy_known_hosts -L OpenWRT-LAN-IP:5080:127.0.0.1:3128 USERNAME@SERVER
The number 5080 is the local port on which the HTTP proxy should be accessible. You may choose to use any different port which is not yet in use instead.
Adjusting configuration of HTTP proxy
Create the file pservice in the /etc/init.d/ directory of the OpenWRT router using WinSCP (of course alternatively the ssh terminal may be used), with the contents of this linked file.
After saving, open the properties of the pservice file and set the access rights to 755.
Then create a second pservice file in the /etc/config/ directory with the following contents:
config pservice
option name 'HTTP-Proxy'
option respawn_maxfail 0
option command /bin/sh
list args -c
list args 'exec sshpass -p "PASSWORD" ssh -N -o UserKnownHostsFile=/root/perfect_privacy_known_hosts -L 192.168.1.1:5080:127.0.0.1:3128 USERNAME@SERVER'
Instead of PASSWORD and USERNAME enter your Perfect Privacy login credentials, and instead of SERVER use a server of your choice (for example basel.perfect-privacy.com).
Then execute the following command using PuTTY or any other terminal program: /etc/init.d/pservice enable
For applications instead of 127.0.0.1:5080 then use 192.168.1.1:5080 to utilize the OpenWRT router.
Tunneling SOCKS proxy through SSH
A SOCKS proxy is very similar to an HTTP proxy in the aforementioned points. But some applications only support one of these two methods. The scheme is:
sshpass -p 'PASSWORD' ssh -N -o UserKnownHostsFile=perfect_privacy_known_hosts -D OpenWRT-LAN-IP:5081 USERNAME@SERVER
5081 is the port on which the proxy should be available locally.
Adjusting configuration of SOCKS proxy
Skip the following steps till the section "Configuring SOCKS proxy", if the file pservice was already created.
Create the file pservice in the /etc/init.d/ directory of the OpenWRT router using WinSCP (of course alternatively the ssh terminal may be used), with the contents of this linked file.
After saving, open the properties of the pservice file and set the access rights to 755.
Then execute the following command using PuTTY or any other terminal program: /etc/init.d/pservice enable
Configuring SOCKS proxy
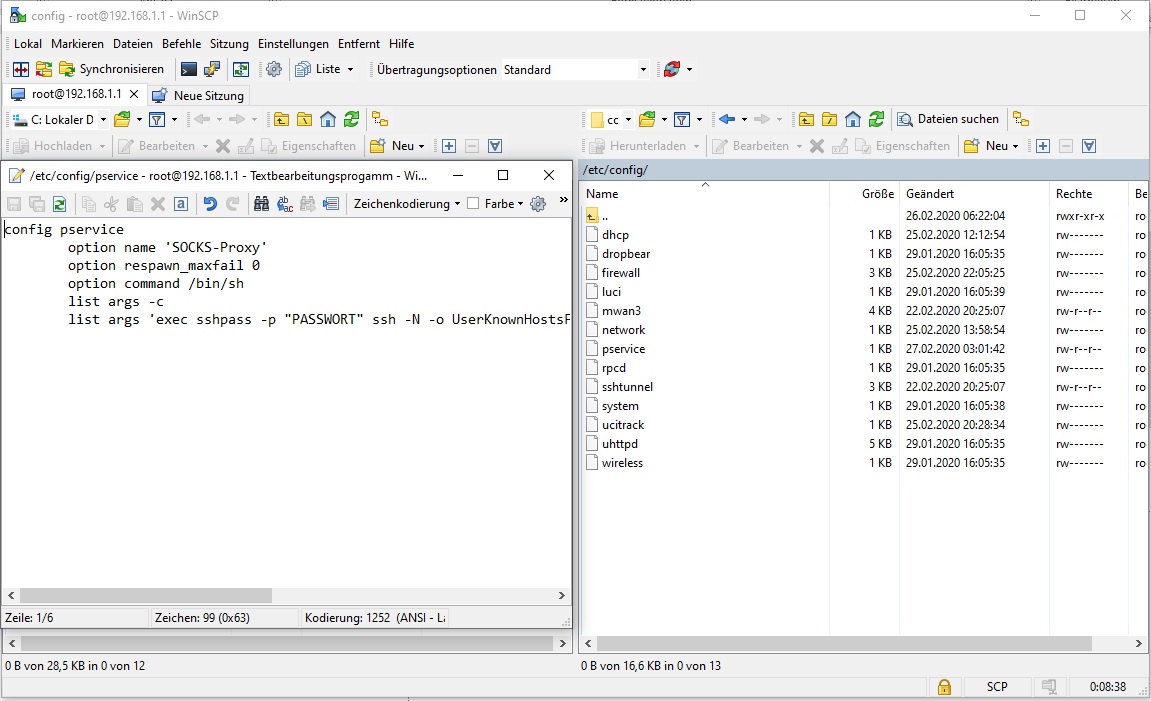
In the pservice file located in the directory /etc/config/ add the following content at the bottom. (If the pservice file does not yet exist, please create it).
config pservice
option name 'SOCKS-Proxy'
option respawn_maxfail 0
option command /bin/sh
list args -c
list args 'exec sshpass -p "PASSWORD" ssh -N -o UserKnownHostsFile=/root/perfect_privacy_known_hosts -D 192.168.1.1:5081 USERNAME@SERVER'
Instead of PASSWORD and USERNAME enter your PerfectPrivacy login credentials, and instead of SERVER use a server of your choice (for example basel.perfect-privacy.com).
For applications instead of 127.0.0.1:5081 then use 192.168.1.1:5081 to utilize the OpenWRT router.
Tunneling Tor proxy through SSH
If you want to get a taste of the Tor network, you can use Perfect Privacy's Tor proxy via SSH. This allows you to access .onion addresses using your normal browser.
The scheme of the SSH connection to use the TOR proxy is like this: sshpass -p 'PASSWORD' ssh -N -o UserKnownHostsFile=perfect_privacy_known_hosts -L OpenWRT-LAN-IP:5083:127.0.0.1:9050 USERNAME@SERVER
If you are using Tor for security and anonymity reasons, we strongly recommend that you do not use your normal browser and use the Tor Browser Bundle instead.
Adjusting configuration of TOR proxy
Skip the following steps till the section "Configuring TOR proxy", if the file pservice was already created.
Create the file pservice in the /etc/init.d/ directory of the OpenWRT router using WinSCP (of course alternatively the ssh terminal may be used), with the contents of this linked file.
After saving, open the properties of the pservice file and set the access rights to 755.
Then execute the following command using PuTTY or any other terminal program: /etc/init.d/pservice enable
Configuring TOR proxy
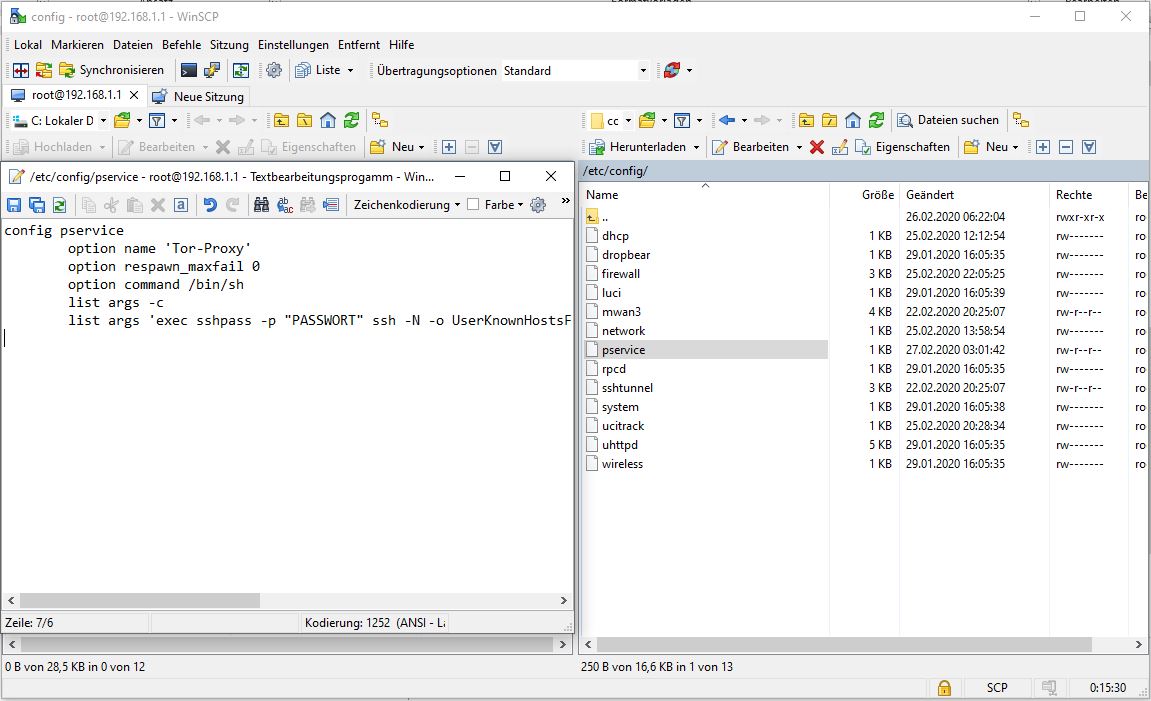
In the pservice file located in the directory /etc/config/ add the following content at the bottom. (If the pservice file does not yet exist, please create it).
config pservice
option name 'Tor-Proxy'
option respawn_maxfail 0
option command /bin/sh
list args -c
list args 'exec sshpass -p "PASSWORT" ssh -N -o UserKnownHostsFile=perfect_privacy_known_hosts -L 192.168.1.1:5083:127.0.0.1:9050 BENUTZERNAME@SERVER'
Instead of PASSWORD and USERNAME enter your PerfectPrivacy login credentials, and instead of SERVER use a server of your choice (for example basel.perfect-privacy.com).
For applications like the TOR browser instead of 127.0.0.1:5083 then use the SOCKS5 setting with 192.168.1.1:5083 to utilize the OpenWRT router.
General port forwarding
At Perfect Privacy SSH usage is not limited to just HTTP, SOCKS and TOR proxies. You can tunnel any connections to other services through SSH and thus hide your IP address from the service providers. The scheme is: sshpass -p 'PASSWORD' ssh -N -o UserKnownHostsFile=perfect_privacy_known_hosts -L OpenWRT-LAN-IP:5082: smtp.gmail.com:465 USERNAME@SERVER
Adjusting configuration of port forwarding
Skip the following steps till the section "Configuring port forwarding", if the file pservice was already created.
Create the file pservice in the /etc/init.d/ directory of the OpenWRT router using WinSCP (of course alternatively the ssh terminal may be used), with the contents of this linked file.
After saving, open the properties of the pservice file and set the access rights to 755.
Then execute the following command using PuTTY or any other terminal program: /etc/init.d/pservice enable
Configuring port forwarding
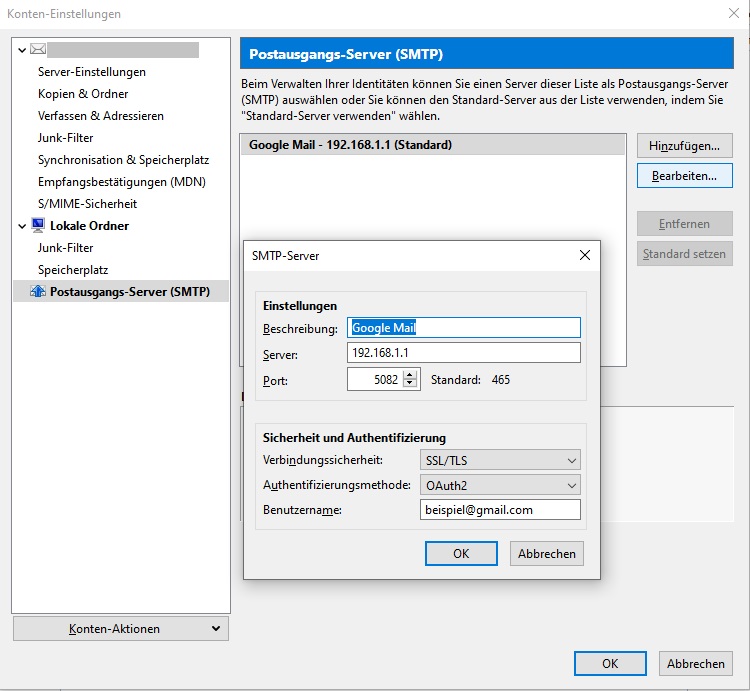
In this example we forward a connection to an SMTP server smtp.gmail.com on port 465 through the SSH tunnel and make the service available locally on port 5082.
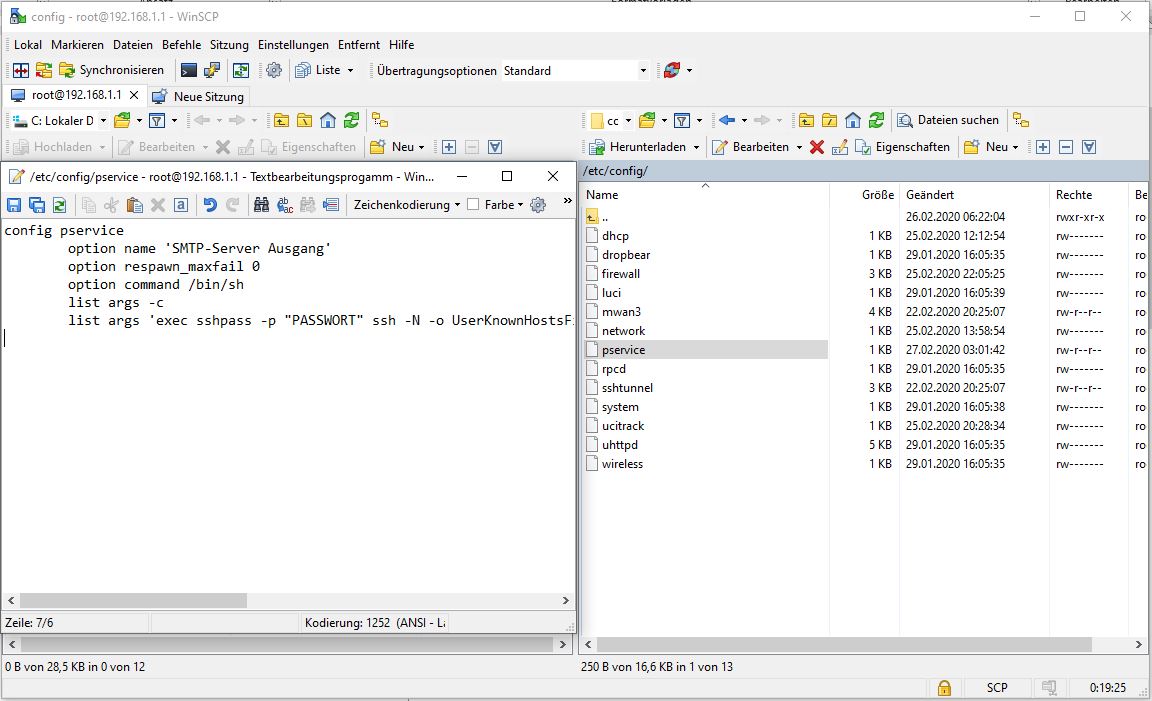
In the pservice file located in the directory /etc/config/ add the following content at the bottom. (If the pservice file does not yet exist, please create it).
config pservice
option name 'SMTP-Server'
option respawn_maxfail 0
option command /bin/sh
list args -c
list args 'exec sshpass -p "PASSWORD" ssh -N -o UserKnownHostsFile=/root/perfect_privacy_known_hosts -L 192.168.1.1:5082:smtp.gmail.com:465 USERNAME@SERVER'
Instead of PASSWORD and USERNAME enter your PerfectPrivacy login credentials, and instead of SERVER use a server of your choice (for example basel.perfect-privacy.com). Replace smtp.gmail.com:465 with the SMTP server data of your choice.
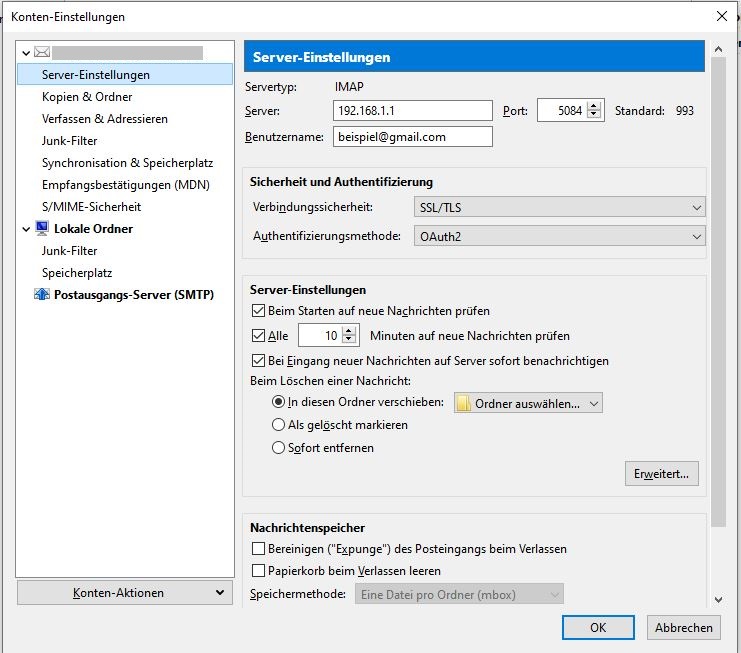
You can configure the server for incoming email in similar manner as the SMTP server for sending emails.
Use the following configuration in the pservice file.
config pservice
option name 'IMAP-Server'
option respawn_maxfail 0
option command /bin/sh
list args -c
list args 'exec sshpass -p "PASSWORD" ssh -N -o UserKnownHostsFile=/root/perfect_privacy_known_hosts -L 192.168.1.1:5084:imap.gmail.com:993 USERNAME@SERVER'
General information: If you want you may use as many SSH tunnels as you want at the same time on OpenWRT. Note here that you have to use a different local port for each one that is already in use. At any time on each port only one service can listen for incoming connections.


Questions?
If you have any questions, comments or other feedback regarding this tutorial, please use the corresponding thread in our community forums.