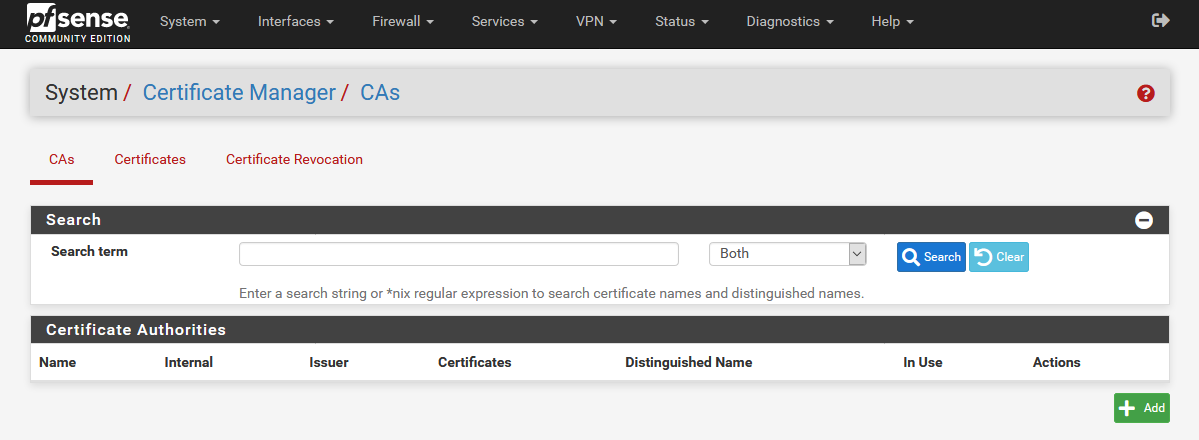
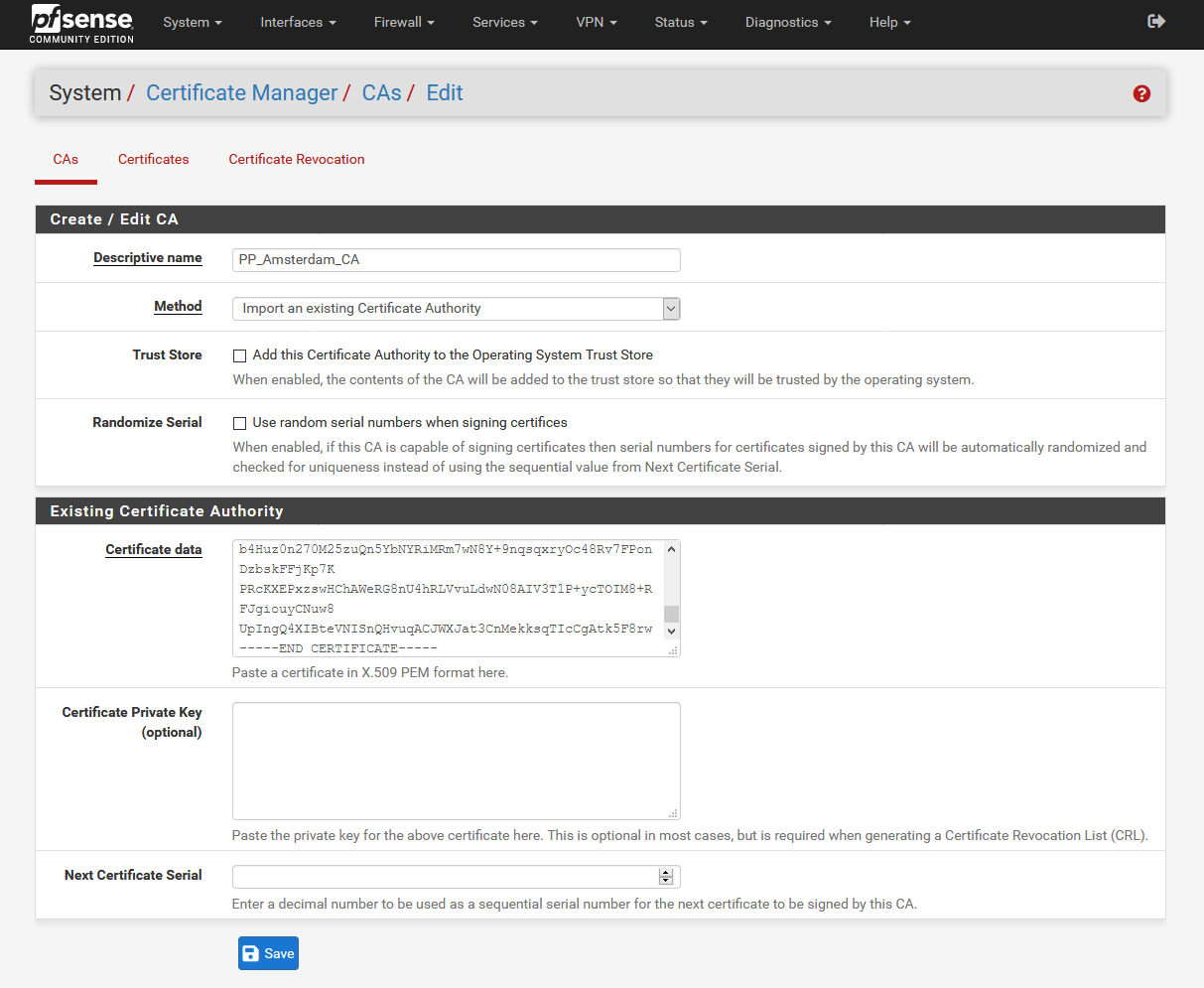
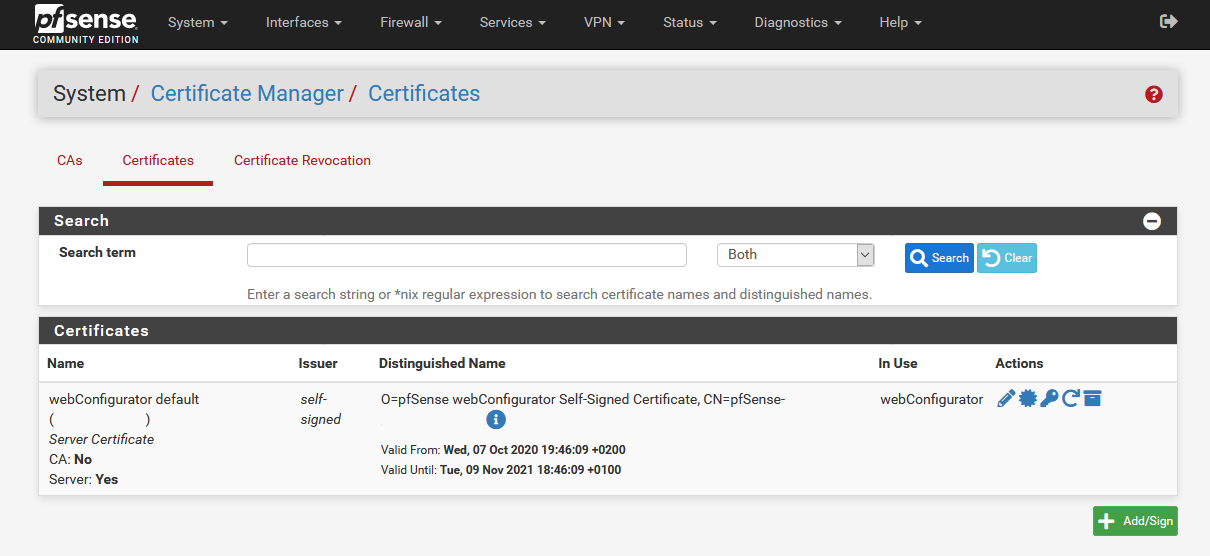
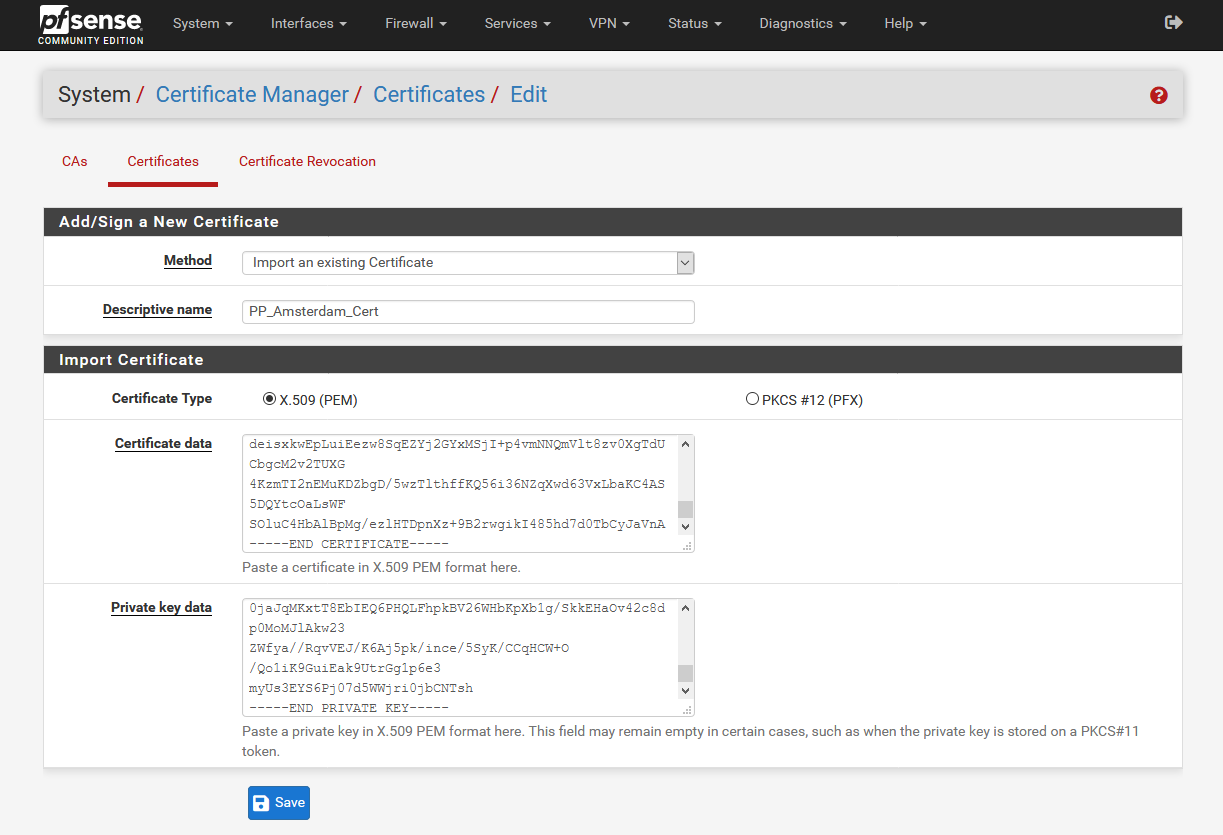
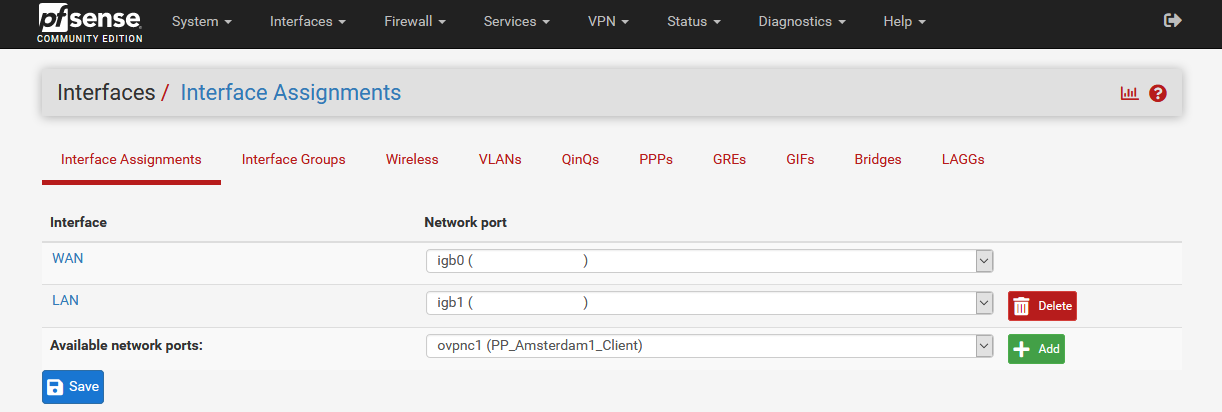
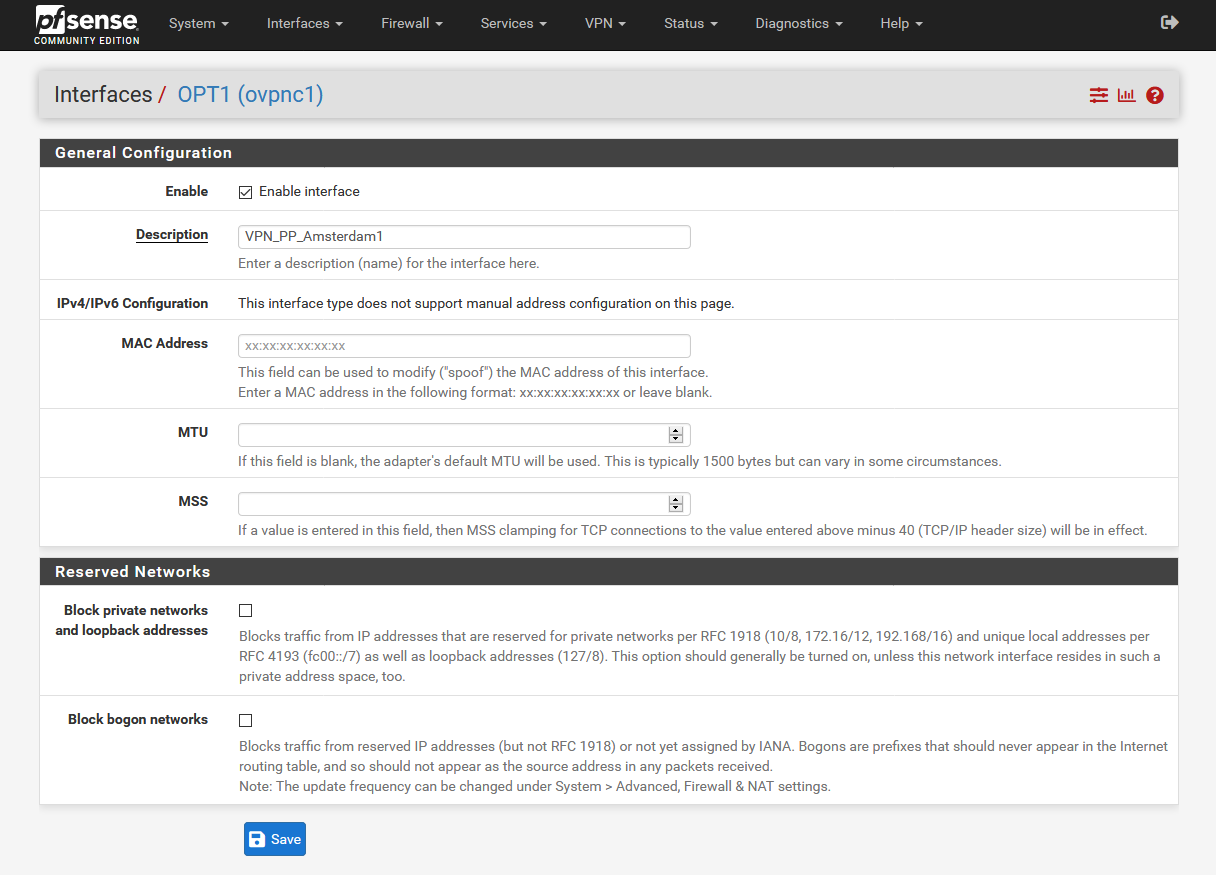
Downloading the OpenVPN configuration files
Download the archive with OpenVPN configuration files and unpack it.
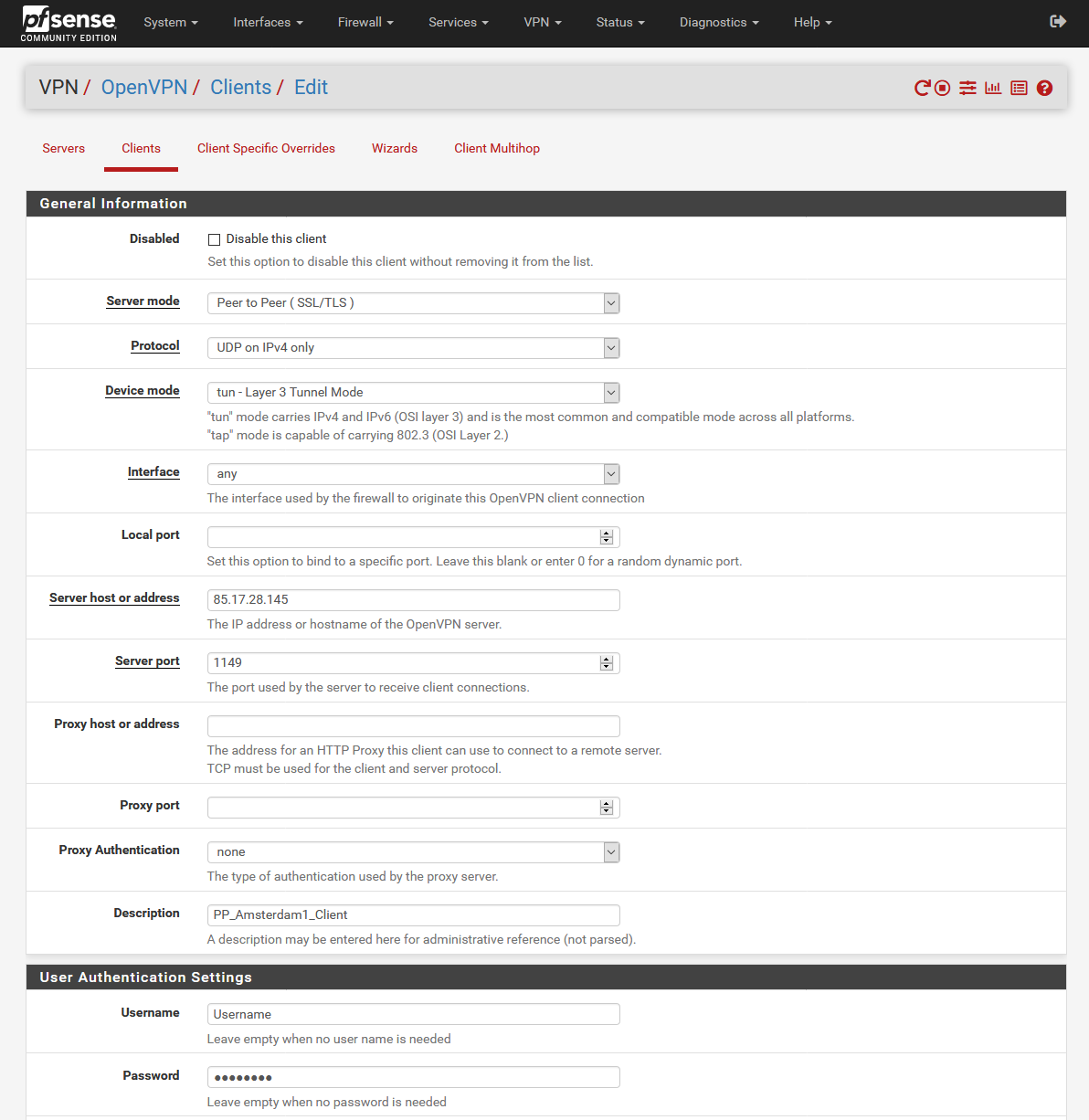
Download View alternate downloads- Protocol:
UDP on IPv4 only - Interface:
WAN - Server Host or Address:
85.17.28.145 oramsterdam1.perfect-privacy.com - Server Port:
1149 - Description:
PP_Amsterdam1_Client - Username:
Your Perfect Privacy username - Password:
Your Perfect Privacy password
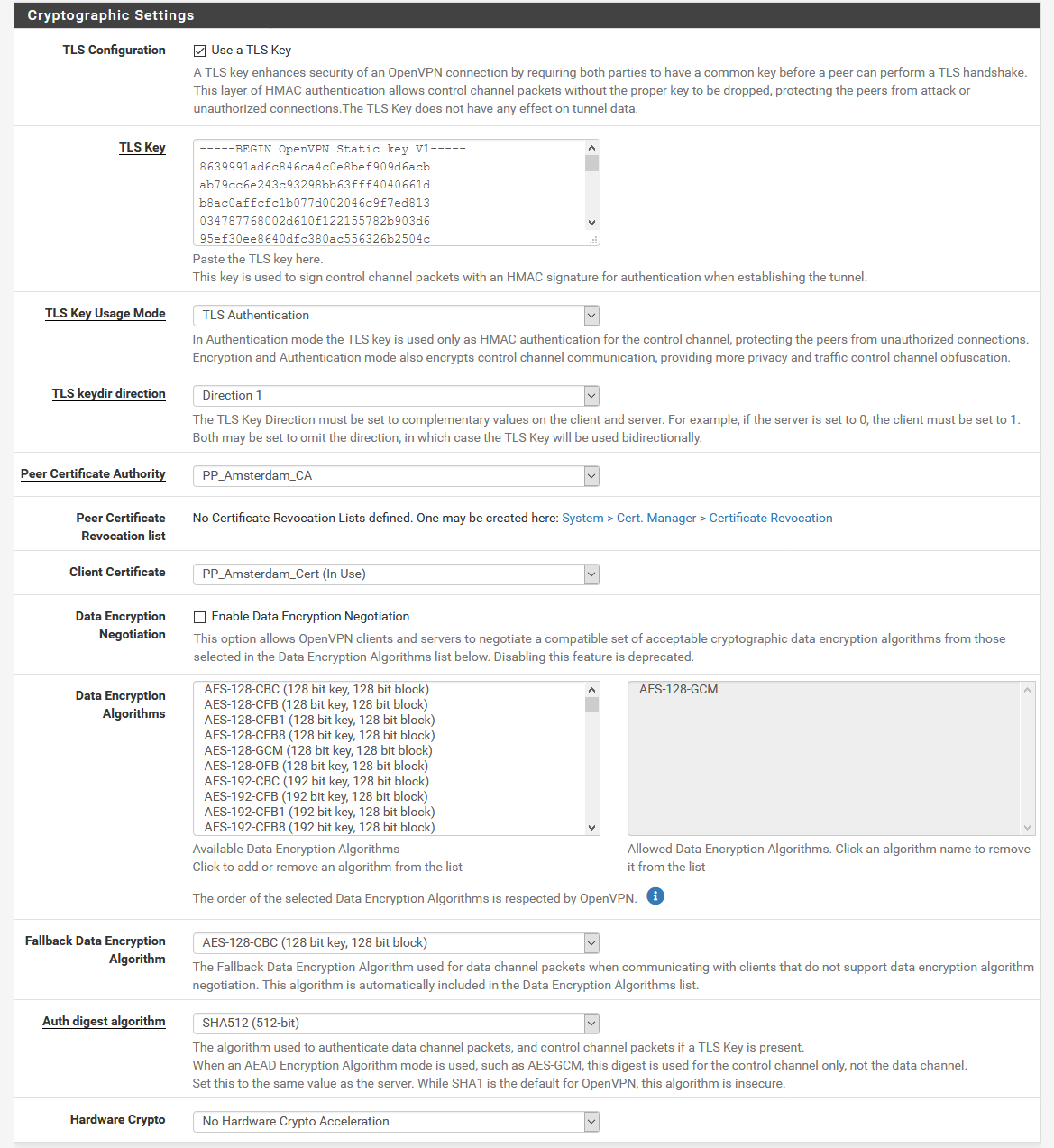
Deactivate the option Automatically generate a TLS Key and copy the text between the <tls-auth></tls-auth> tags from the *.conf file into the field TLS Key.
- TLS keydir direction:
Direction 1 - Peer Certificate Authority:
PP_Amsterdam_CA - Client Certificate:
PP_Amsterdam_Cert
Tip: Depending on the CPU performance on your router you may want to use the weaker encryption AES-128-CBC to get better speed and bandwidth. In this case choose AES-128-CBC for Encryption Algorithm.
- Enable NCP:
Deactivate - Auth digest algorithm:
SHA512
- Compression:
Allow Compression: Refuse any non-stub compression (Most secure) - Topology:
Subnet – One IP address per client
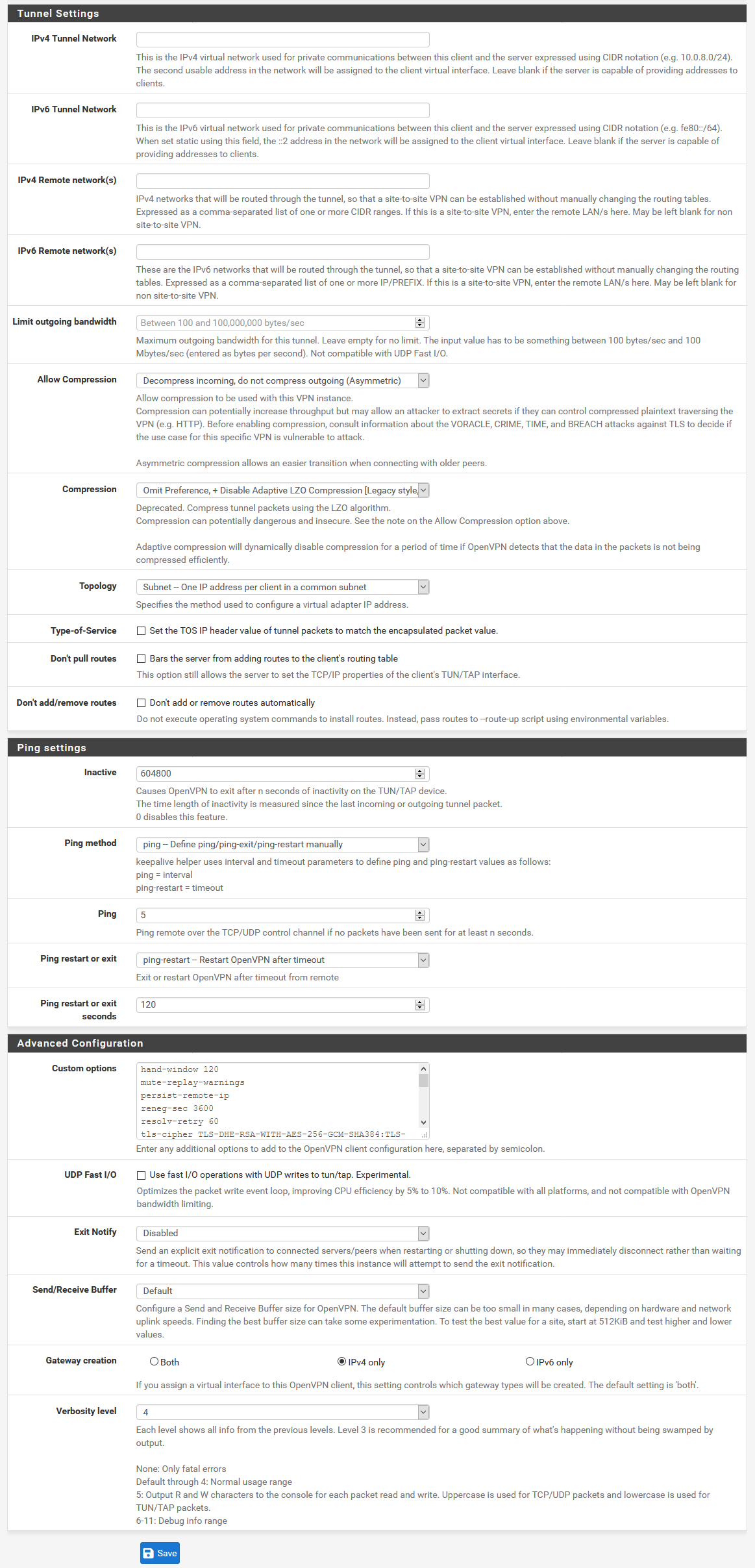
Ping settings
- Inactive:
604800 - Ping method:
ping – Define ping/ping-exit/ping-restart manually - Ping:
5 - Ping restart or exit:
ping-restart – Restart OpenVPN after timeout - Ping restart or exit seconds:
120
Advanced Configuration
Copy the following text block into the field Custom options:
hand-window 120
mute-replay-warnings
persist-remote-ip
reneg-sec 3600
resolv-retry 60
tls-cipher TLS_CHACHA20_POLY1305_SHA256:TLS-DHE-RSA-WITH-AES-256-GCM-SHA384:TLS-DHE-RSA-WITH-AES-256-CBC-SHA:TLS-DHE-RSA-WITH-AES-128-GCM-SHA256:TLS-DHE-RSA-WITH-AES-128-CBC-SHA:TLS_AES_256_GCM_SHA384:TLS-RSA-WITH-AES-256-CBC-SHA
tls-timeout 5
tun-mtu 1500
fragment 1300
mssfix
remote-cert-tls server- Gateway creation: Select "IPv4 only" (Select "Both" if you want to add IPv6)
- Verbosity level:
4
Now click on the Save button.
This step is only required for an IPv6 connection. Skip it if you don't want to use IPv6.
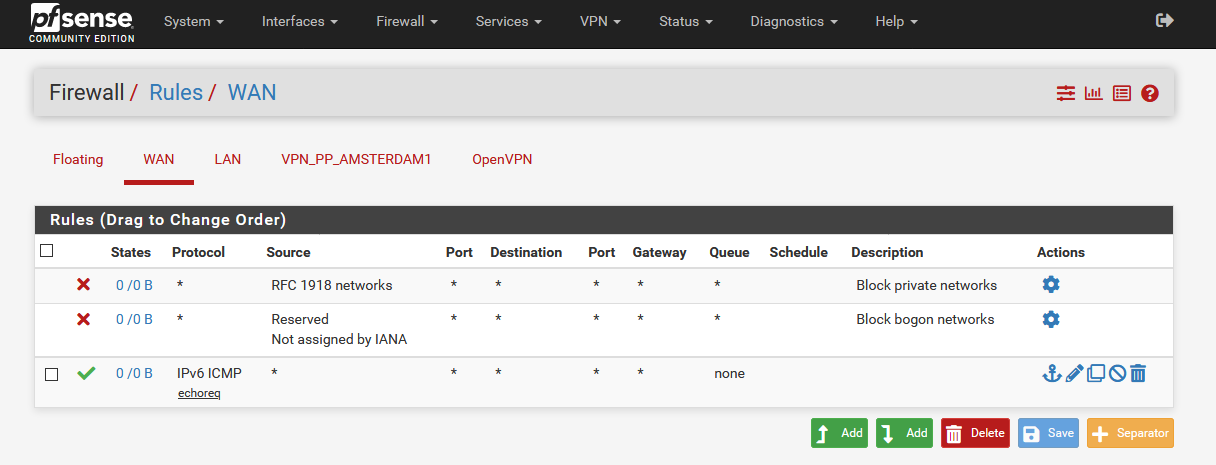
Navigate to the menu Firewall → Rules → WAN and create an ICMP rule for the IPv6 protocol with the following options:
- Action:
Allow - Interface:
WAN - Address Family:
IPv6 - Protocol:
ICMP - ICMP Subtype:
Echo request - Source:
all - Destination:
all
Click on the Save button.
Set up DNS-Leak protection
If you want to access the Internet without VPN as well you should configure public name servers, for instance those from Cloudflare, Google or any from the OpenNIC-Project. If the VPN is connected, DNS requests will be sent anonymously over the VPN tunnel.
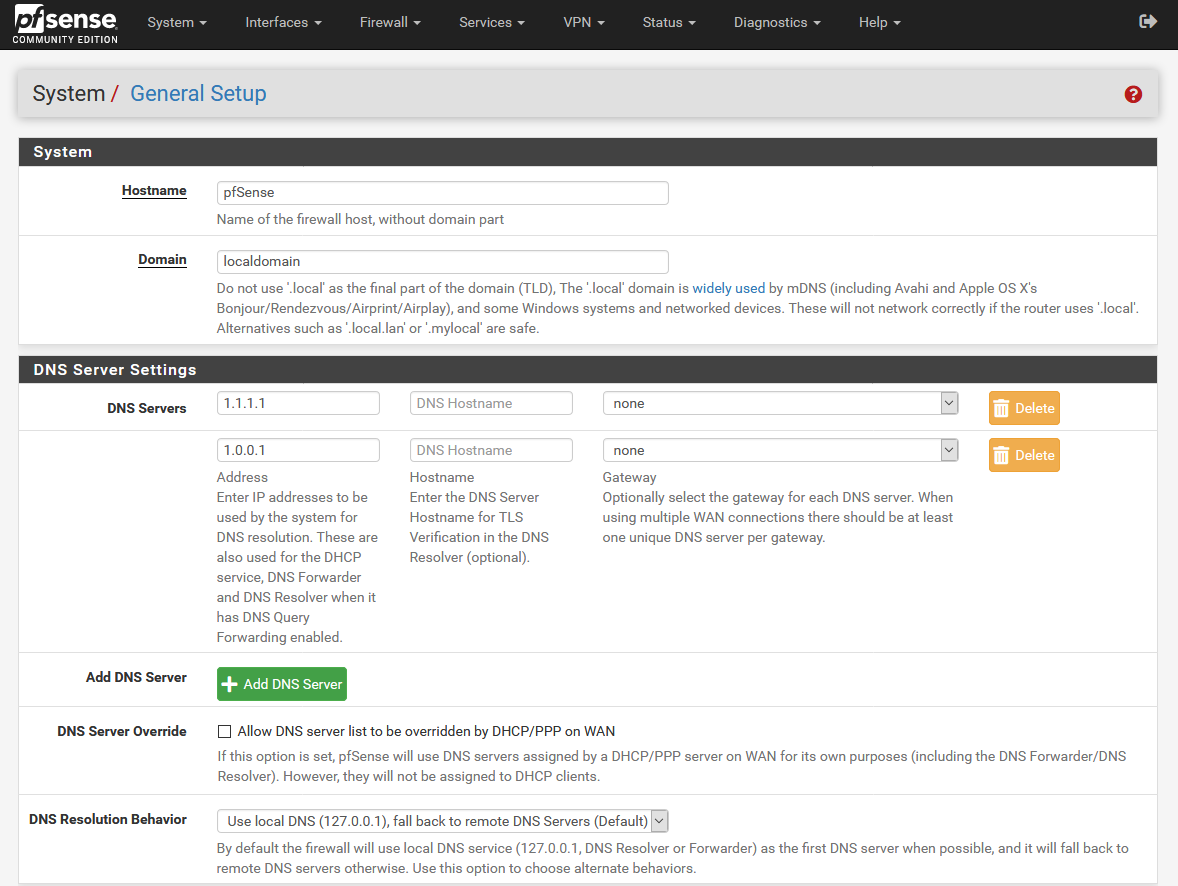
Go to the menu System → General Settings and enter at least two DNS servers of your choice. In this example we are using the DNS servers 1.1.1.1 and 1.0.0.1.
To configure DNS servers for IPv6 too, click on the button + Add DNS Server and enter for example 2606:4700:4700::1111 and 2606:4700:4700::1001 as DNS servers.
Deactivate the option DNS Server Override. Leave the other settings as they are.
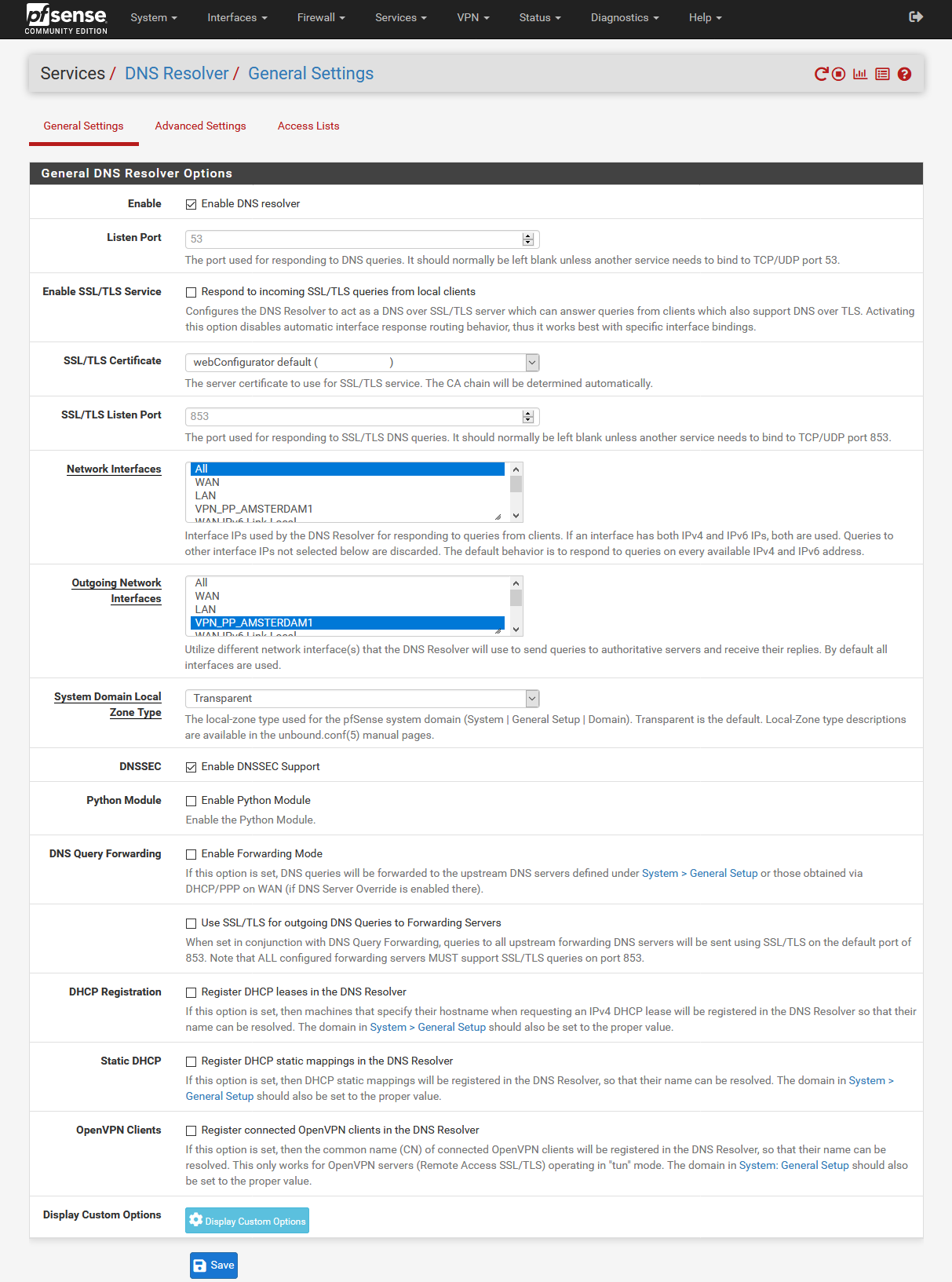
Use the menu to go to Services → DNS Resolver and at Outgoing Network Interfaces select
Configure the following option:
- DNSSEC:
Enable DNSSEC Support
Note: With the default settings DNS queries are sent directly to the internet servoce provider, therefore it is important to select a VPN interface as outgoing network interface for DNS queries to prevent DNS leaks.
Set up Kill Switch
CAUTION: This step will activate the firewall protection (leak protection or „kill switch“).
If you proceed with these steps, the Internet connection will only work when a VPN tunnel has been established.
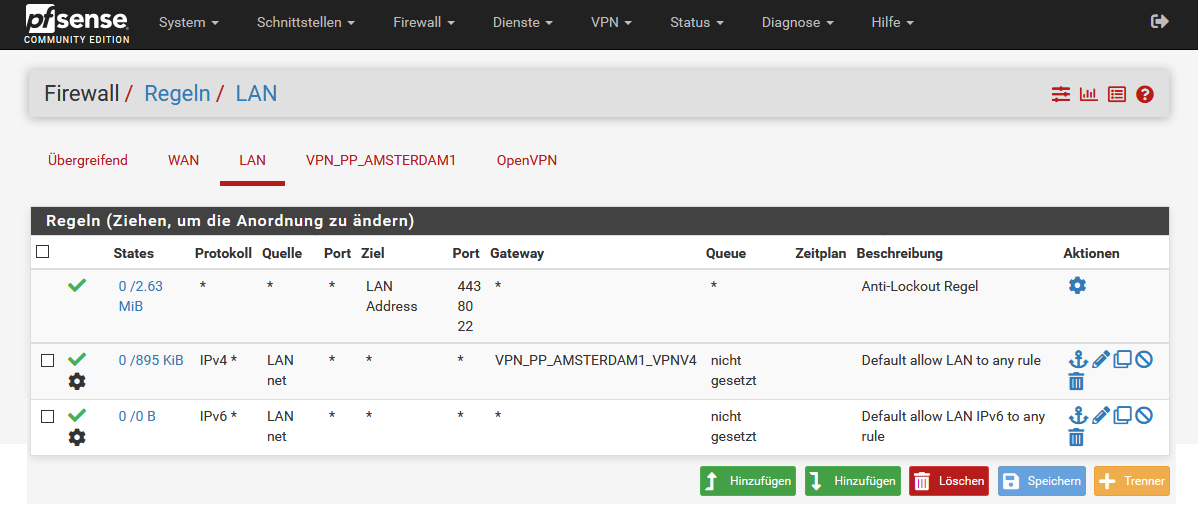
Navigate to Firewall → Rules → LAN and deactivate the rule for IPv6 (if the use of IPv6 is not desired) and click on the Save button.
Then open the IPv4 rule by clicking on the pen symbol (Edit). Activate Advanced options at the bottom. At Tag enter:
(If needed repeat this step for the IPv6 rule. Otherwise deactivate the IPv6 rule.)
The traffic thereby is happening via the selected gateways only.
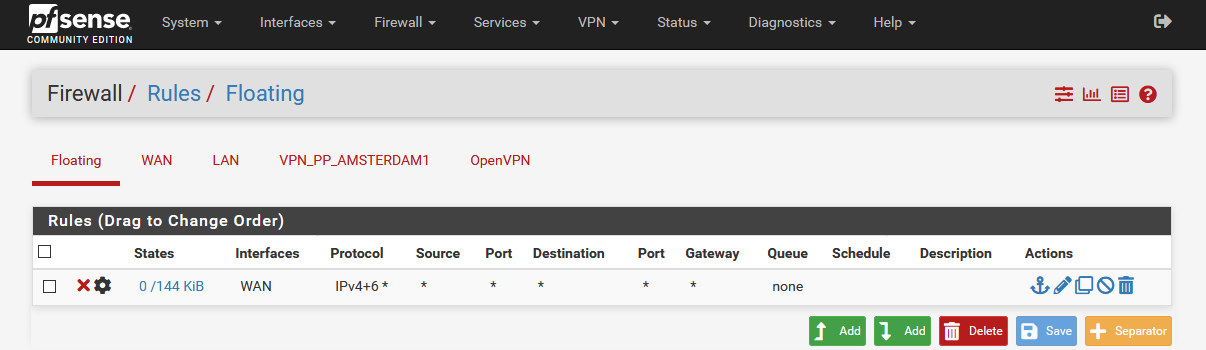
Now a floating rule is required to ensure all traffic is blocked in case the OpenVPN connection is offline.
Change to Firewall → Rules → Floating and create a new block-rule at the bottom with the following settings:
- Action:
Block - Interface:
WAN - Direction:
all - Address Family:
IPv4+IPv6 - Protocol:
all - Source:
all - Destination:
all - Marked/Tagged:
NO_WAN_EGRESS
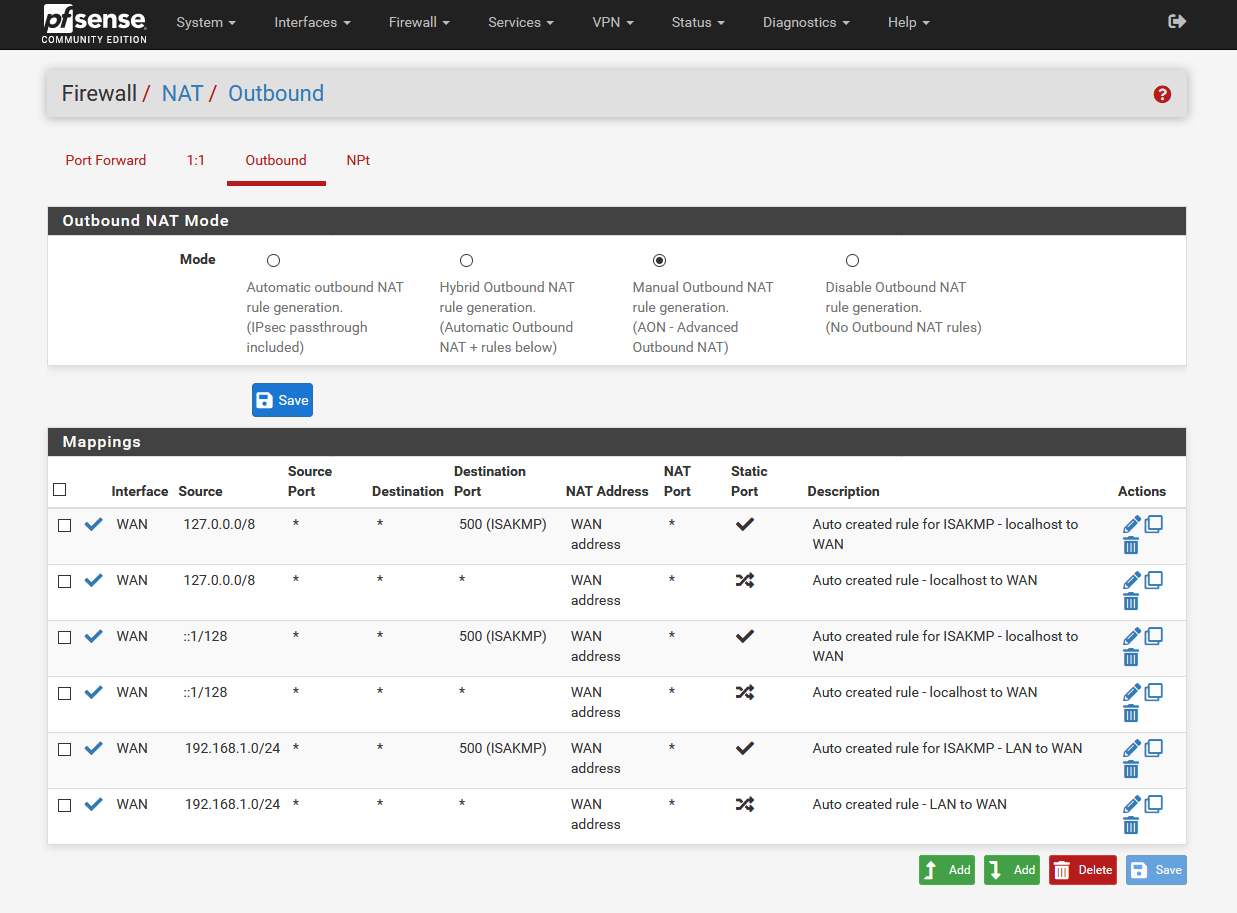
Go to the menu Firewall → NAT → Outbound and select the option Manual Outbound NAT rule generation and click on Save.
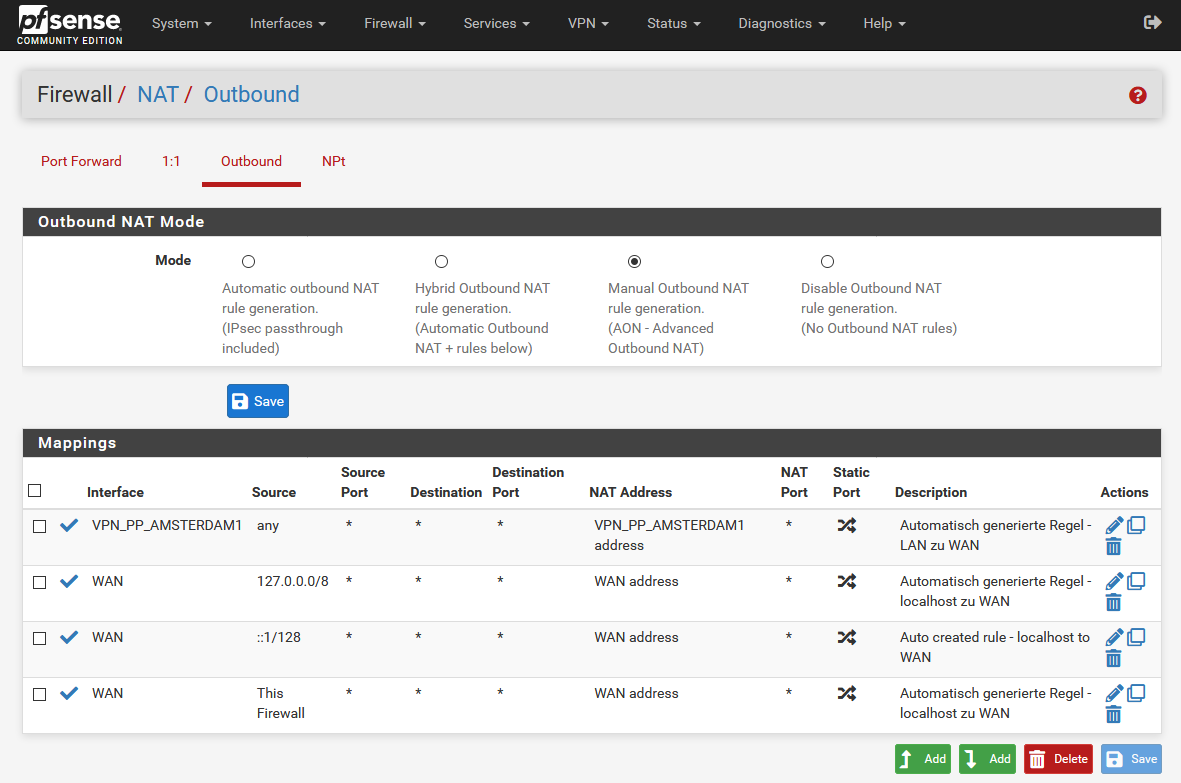
The pfSense then generates a set of outbound NAT rules, as shown in the image on the left. Remove all of them execpt for three NAT rules:
- 127.0.0.0/8 ... Auto created rule – localhost to WAN
- ::1/128 ... Auto created rule – localhost to WAN
- 192.168.1.0/24 ... Auto created rule – LAN to WAN
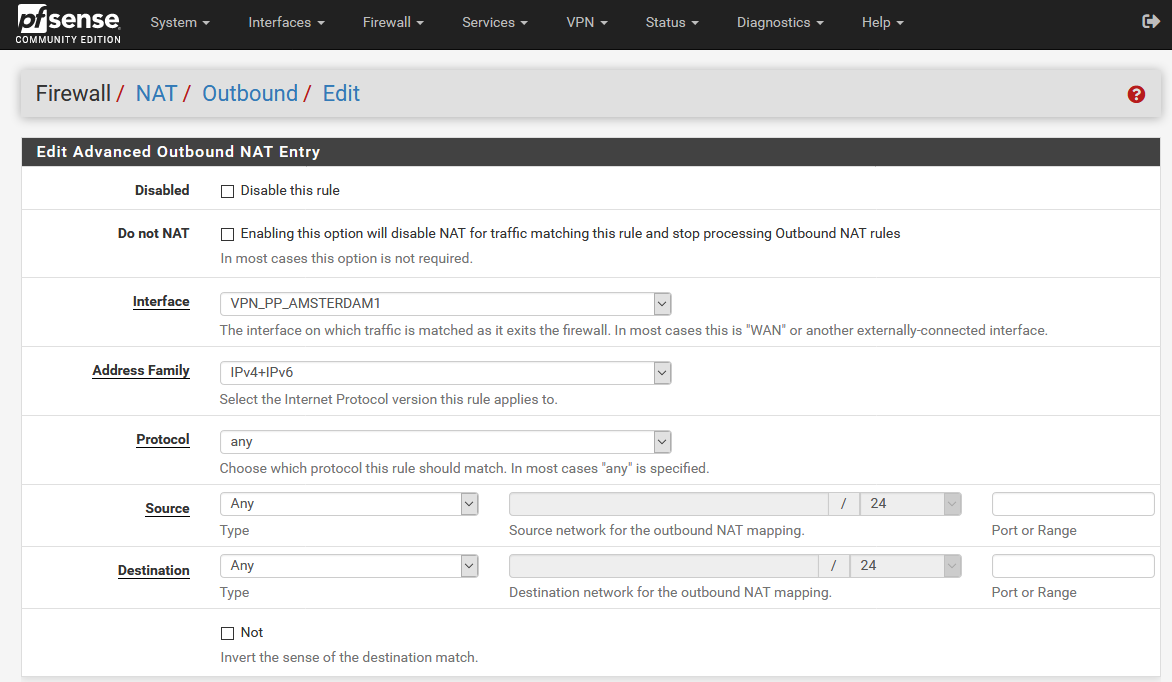
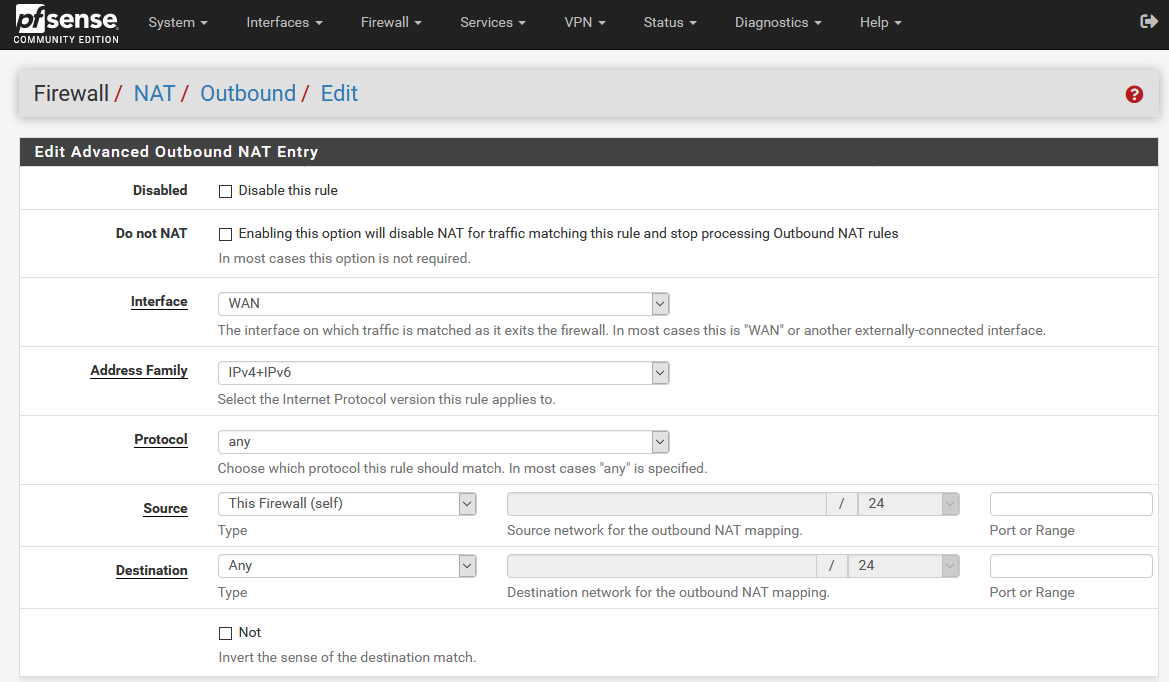
Edit the LAN to WAN rule (192.168.1.0/24) by clicking on the pen icon.
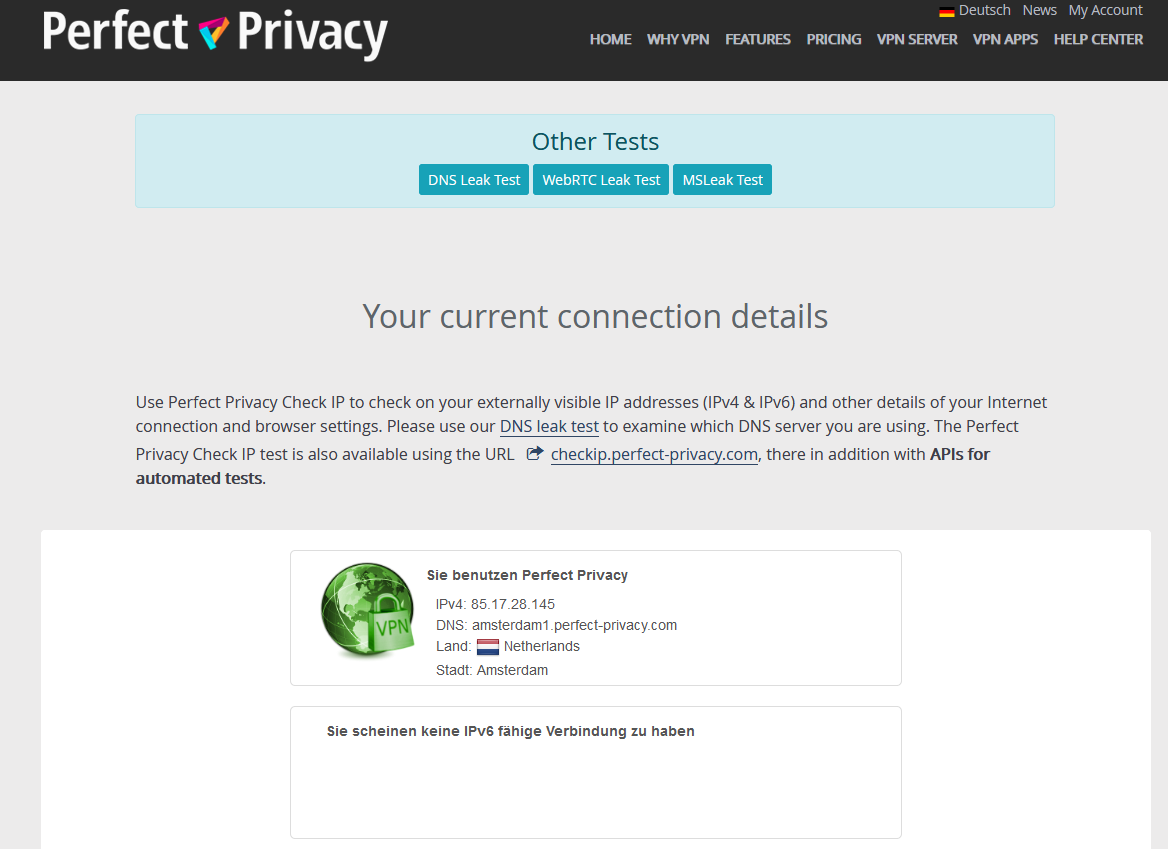
Check VPN connection
You can verify that the VPN connection is working properly by visiting our Check IP website on any device connected to the Internet via the pfSense router.


Questions?
If you have any questions, comments or other feedback regarding this tutorial, please use the corresponding thread in our community forums.