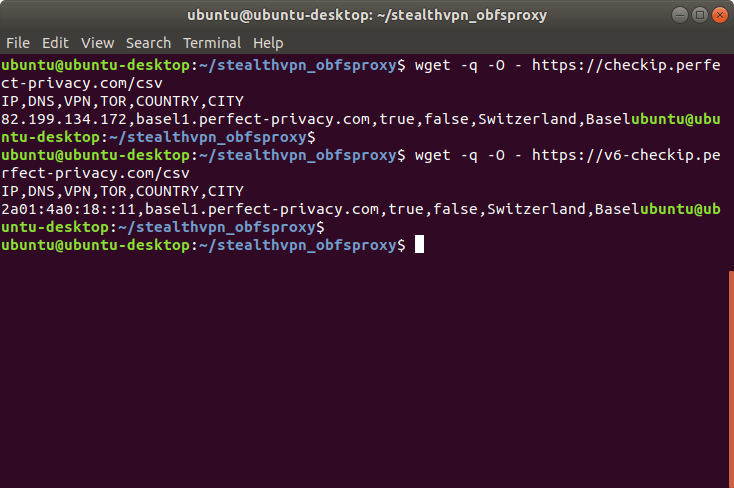
If you cannot connect with OpenVPN, you are probably on a network that blocks VPN connections. With Stealth VPN, you still have the ability to break out of such networks.
With the help of these instructions you can establish an OpenVPN connection which is obfuscated using obfsproxy.
You will need the following software:
- openvpn - for the VPN connection
- obfsproxy - to hide the OpenVPN connection
- resolvconf - to avoid DNS leaks
- wget - to download VPN profiles and check the connection
- unzip - to unzip the VPN profiles
In the example we use Ubuntu 18.04, where the necessary packages have to be installed as follows:
sudo apt update && sudo apt install openvpn obfsproxy resolvconf
Download OpenVPN profiles
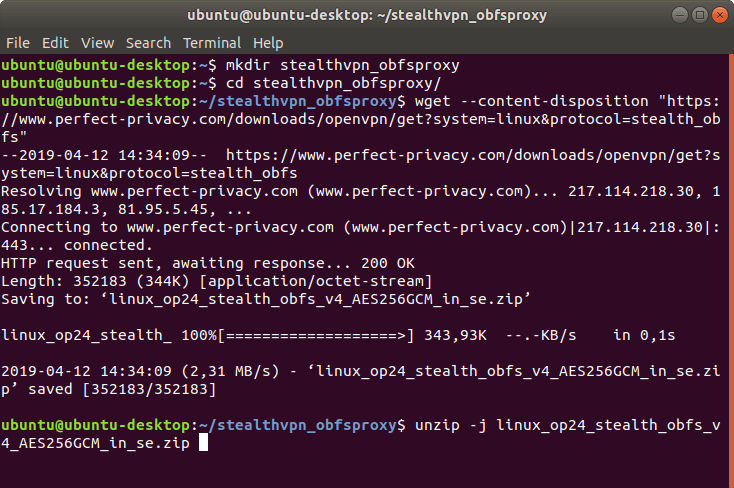
First download the OpenVPN profiles for use with obfsproxy and extract it. We will create a new directory for this.
mkdir stealthvpn_obfsproxy
cd stealthvpn_obfsproxy
wget --content-disposition "https://www.perfect-privacy.com/downloads/openvpn/get?system=linux&protocol=stealth_obfs"
unzip -j linux_op24_stealth_obfs_v4_AES256GCM_AU_in_se.zip
If you have special requirements, you can download OpenVPN configurations with advanced options in the download area.
Start OpenVPN
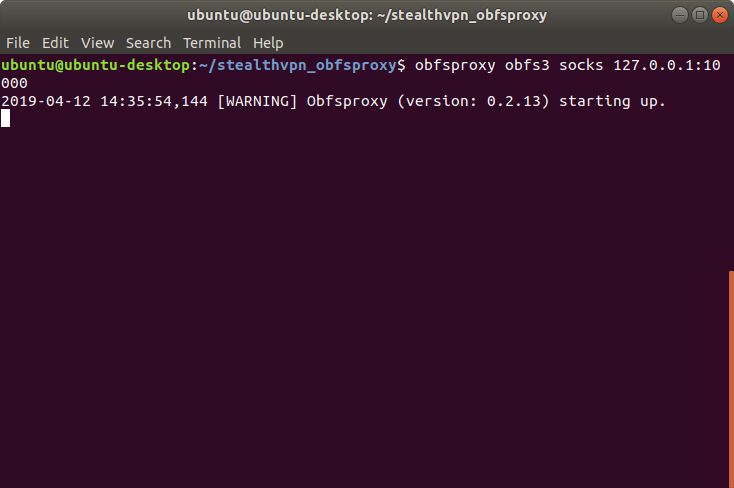
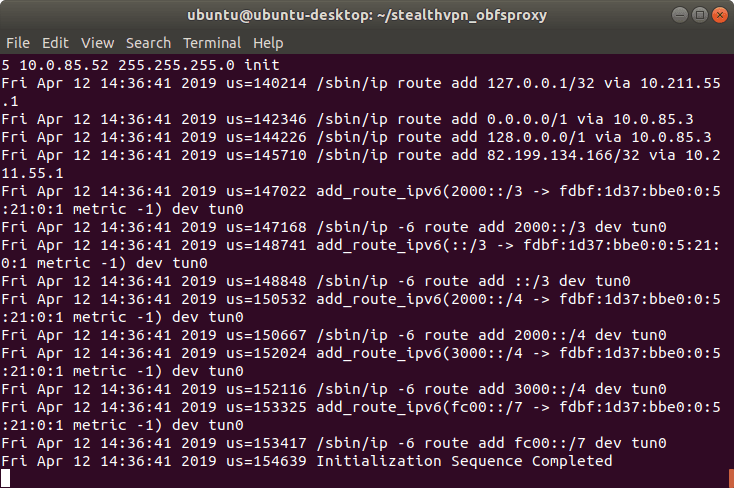
Now you can start OpenVPN in a new terminal:
sudo openvpn VPN_PROFILE
Instead of VPN_PROFILE, use a configuration file of your choice (file extension .conf). In the example we use Basel1.conf.
Our tip: Choose a location that is geographically as close as possible to achieve the best speed.


Questions?
If you have any questions, comments or other feedback regarding this tutorial, please use the corresponding thread in our community forums.