If you cannot connect with OpenVPN, you are probably on a network that blocks VPN connections. With Stealth VPN, you still can break out of such networks.
Using this guide, you create an OpenVPN connection that is obfuscated by stunnel.
You will need the following software:
- openvpn - for the VPN connection
- stunnel - to obfuscate the OpenVPN connection
- resolvconf - to avoid DNS leaks
- wget - to download VPN profiles and check the connection
- unzip - to unzip the VPN profiles
- nano - to change configuration files
In the example we use Ubuntu 18.04, where the necessary packages have to be installed as follows:
sudo apt update && sudo apt install openvpn resolvconf stunnel
Download OpenVPN profiles
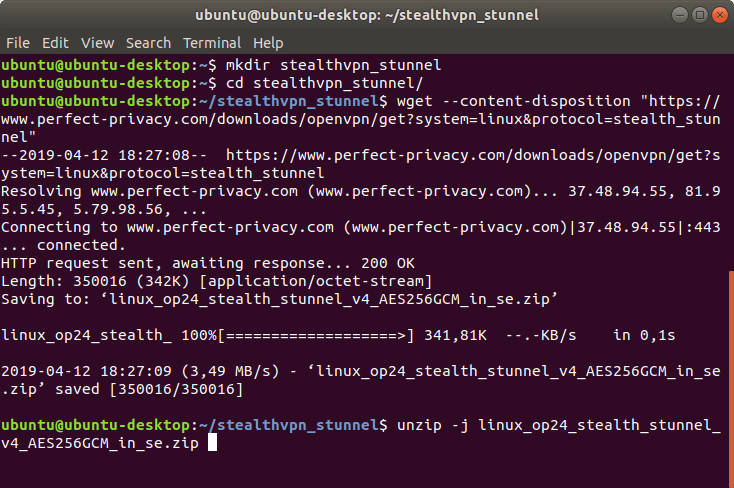
First download the OpenVPN profiles for using stunnel and extract them. We will create a new directory.
mkdir stealthvpn_stunnel
cd stealthvpn_stunnel
wget --content-disposition "https://www.perfect-privacy.com/downloads/openvpn/get?system=linux&protocol=stealth_stunnel"
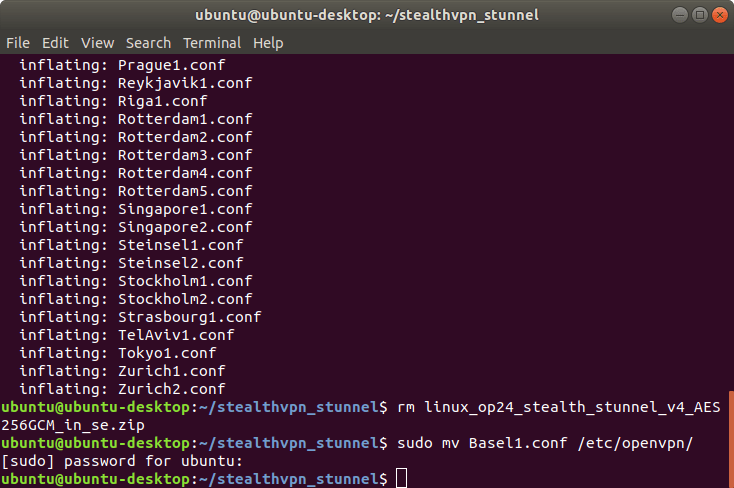
unzip -j linux_op24_stealth_stunnel_v4_AES256GCM_AU_in_se.zip
If you have special demands, you can download OpenVPN configurations with further options in the download area (login required).
Set up OpenVPN and stunnel
Select a server location to which you want to establish the VPN connection.
Our tip: Choose a location that is geographically as close as possible to achieve the best speed.
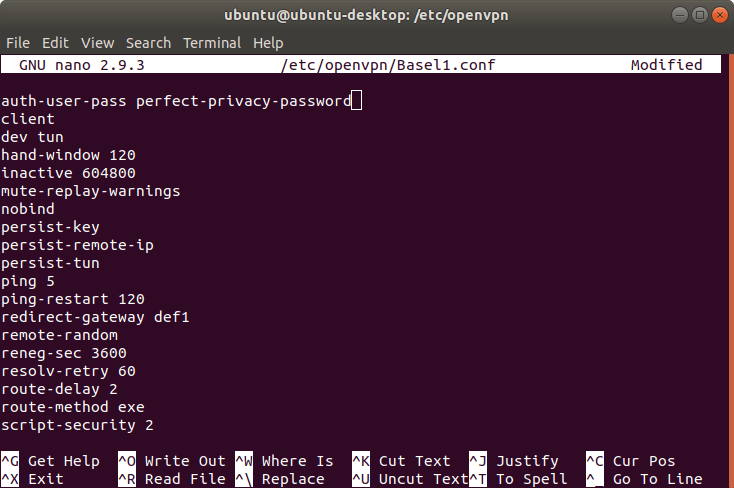
Copy the desired configuration file into the OpenVPN directory. In this example, we have decided to use Basel1.
sudo cp Basel1.conf /etc/openvpn/
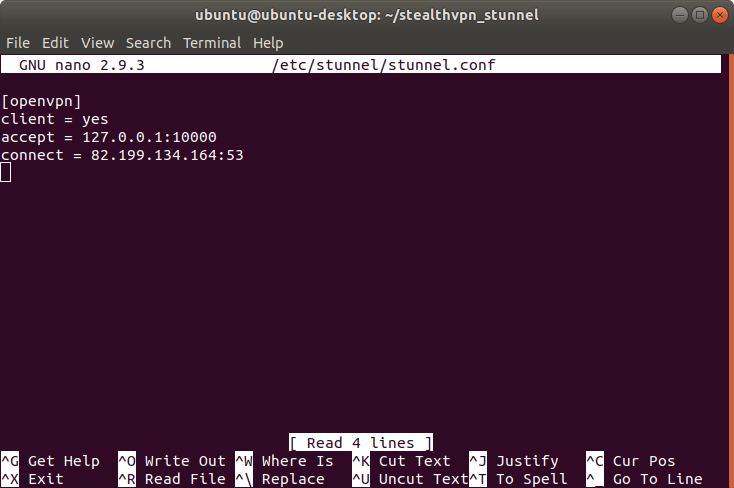
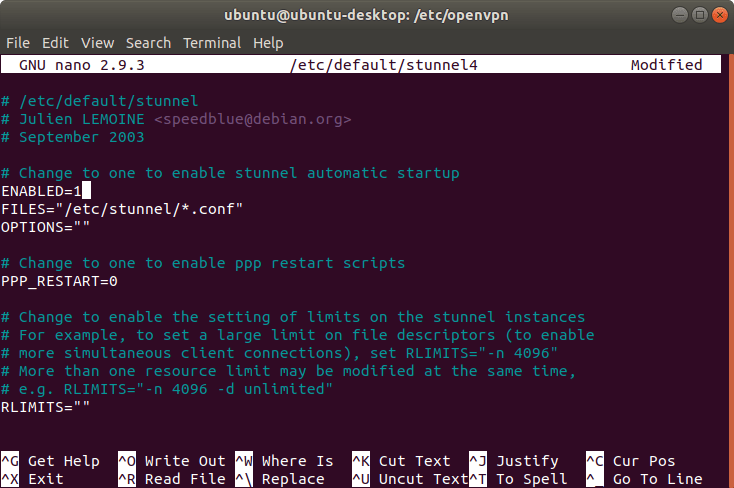
To set up stunnel, create a new configuration file.
sudo nano /etc/stunnel/stunnel.conf
Insert the following content there:
[openvpn]
client = yes
accept = 127.0.0.1:10000
connect = SERVER_IP:TUNNEL_PORT
Replace the SERVER_IP with the stunnel-specific IP address of the respective server. You can look it up in the overview of stunnel ports and IPs.
For the STUNNEL_PORT you can choose between the following ports: 22, 53, 443, 8085, 9009, 36315. To circumvent blocking, ports 53 and 443 are particularly recommended.
Now you only have to tell OpenVPN the configuration that should be started automatically at system startup.
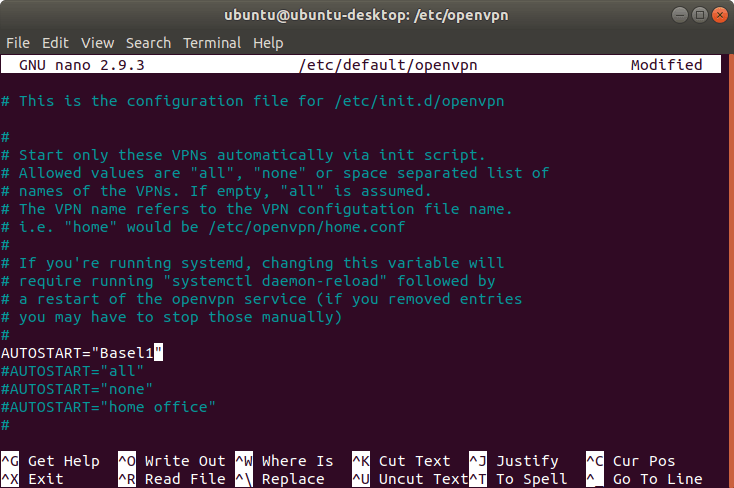
Open the OpenVPN configuration file:
sudo nano /etc/default/openvpn
Insert the following line:
AUTOSTART="Basel1"Make sure that all other AUTOSTART lines are commented out (# at the beginning of the line).
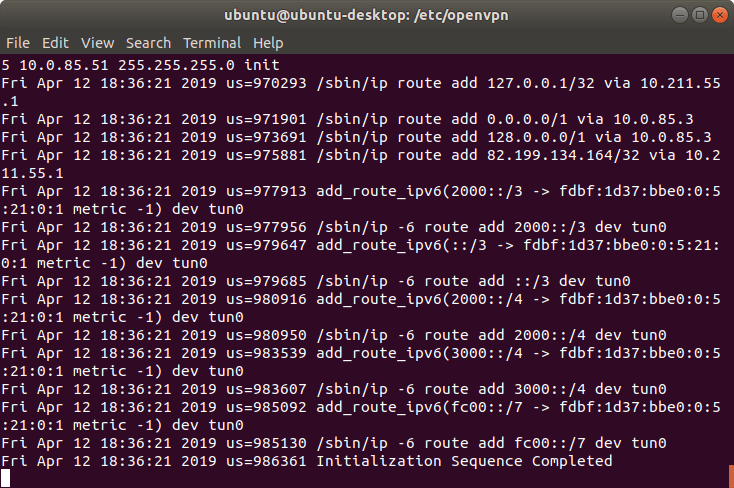
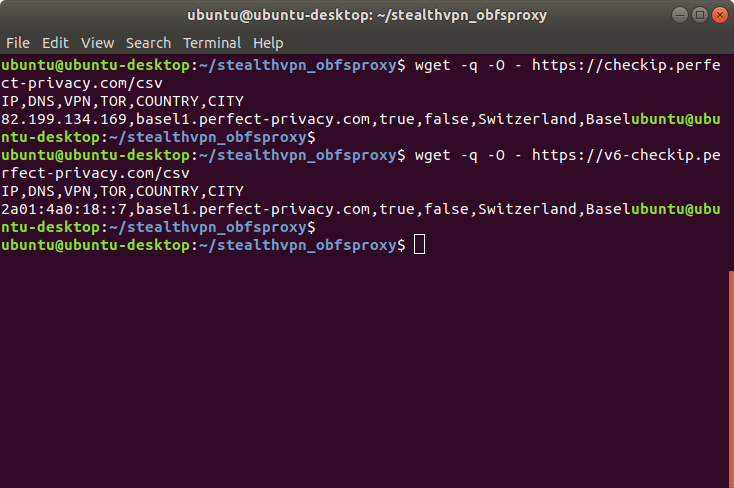
To test the autostart, restart your computer and go to the CheckIP page to test the connection.


Questions?
If you have any questions, comments or other feedback regarding this tutorial, please use the corresponding thread in our community forums.