Install OpenVPN for Android
Also install OpenVPN for Android by Arne Schwabe on Google Play.
Download OpenVPN profile
Download the preferred profile directly onto your smartphone. You can also scan the QR code below.
Our tip: Choose a location that is geographically as close as possible to achieve the best speed.
Set up SSLDroid
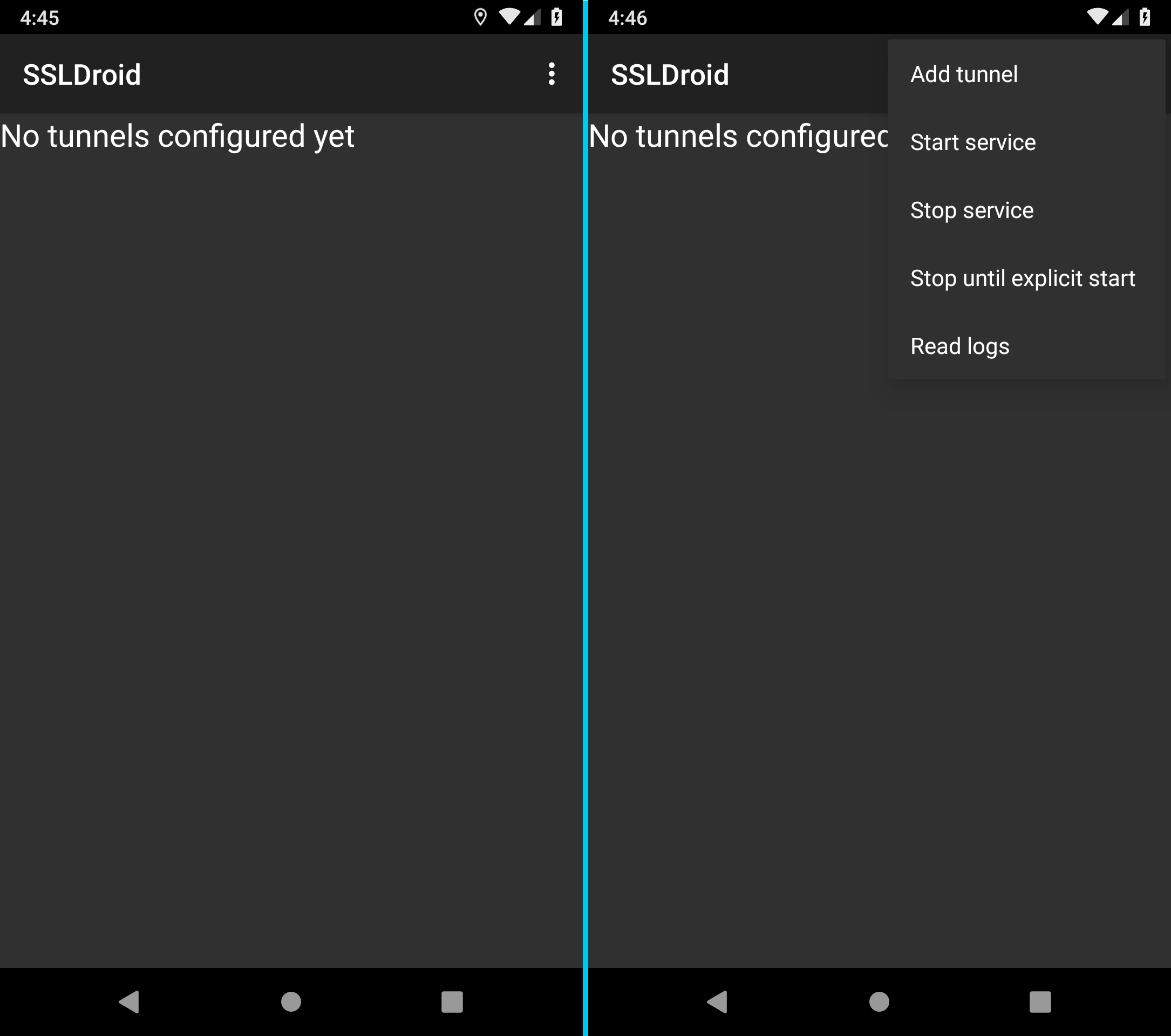
Open SSLDroid and tap the kebab menu at the top right (three dots).
Select Add tunnel.
You have already downloaded the OpenVPN profile for a server location above.
Now search for the corresponding IP address on the OpenVPN with Stealth VPN (stunnel) page.
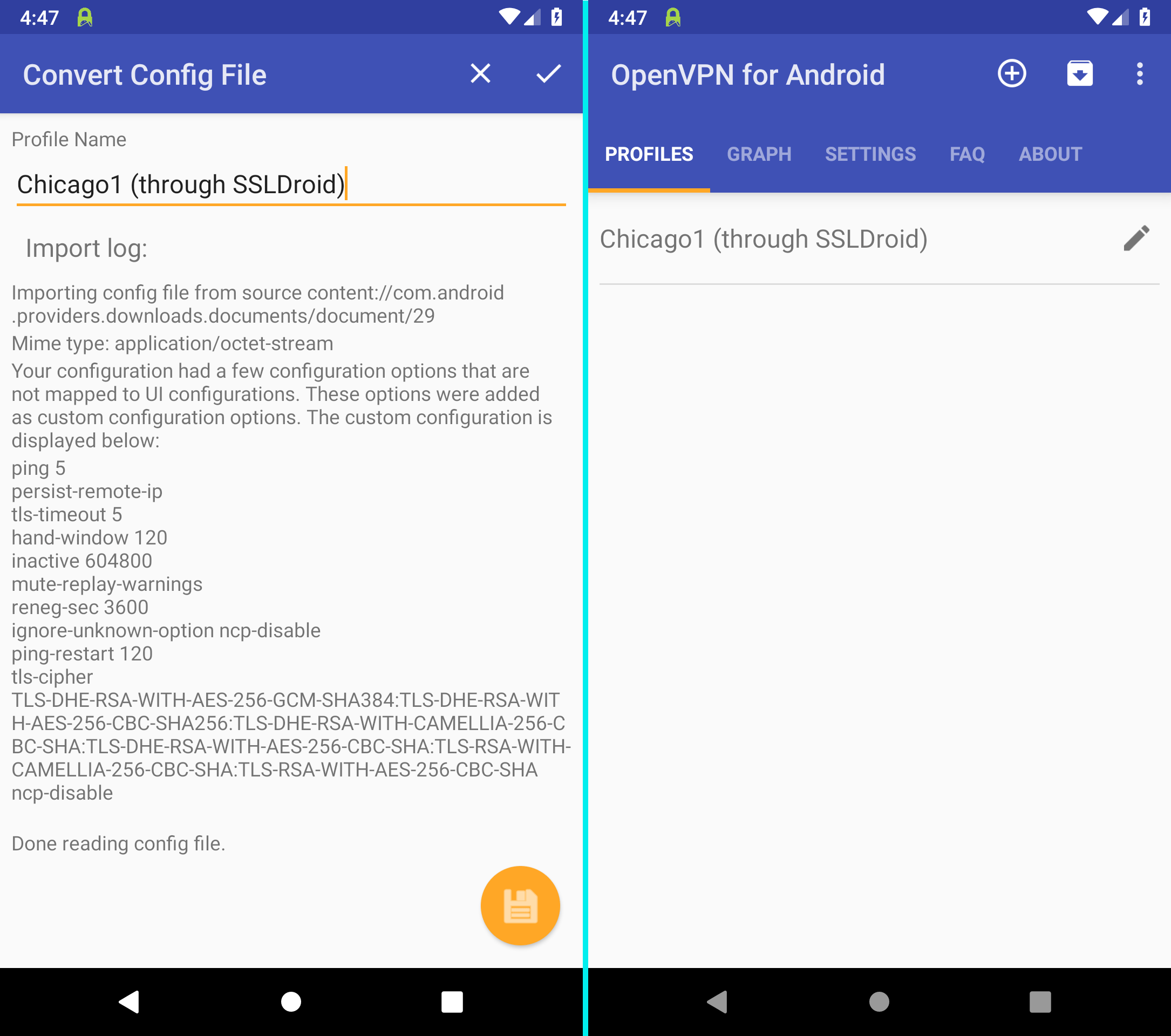
In the example we have chosen Chicago1.
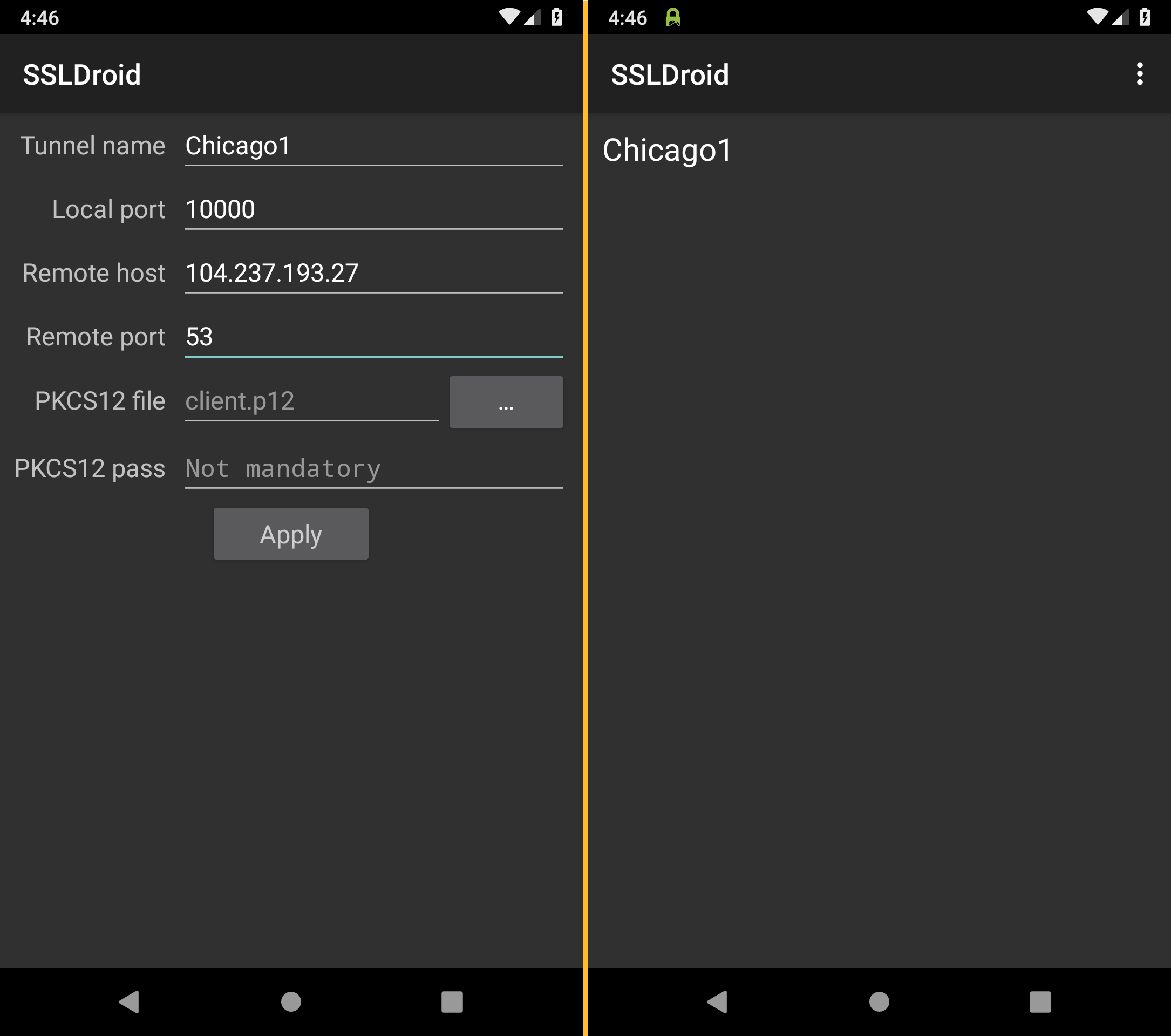
Please now configure SSLDroid as follows:
- Tunnel name:
Name of the server location - Local port:
10000 - Remote host:
The IP address you just looked up - Remote port:
53
Confirm the configuration with Apply.
Touch the new configuration and wait until the SSL connection has been established. You can recognize this by the green SSLDroid icon in the system bar even when the app is closed.
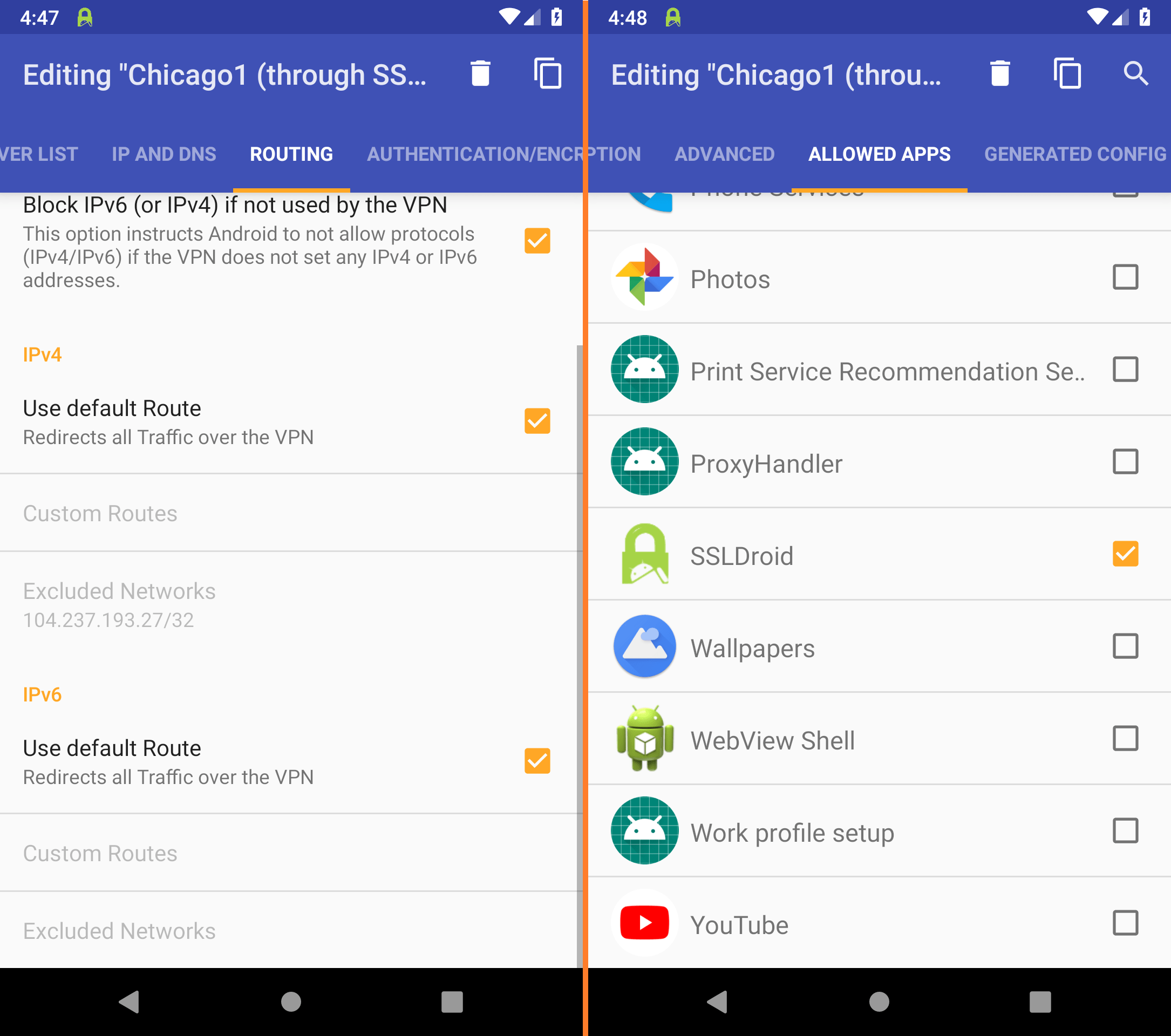
Set up the OpenVPN connection
If the SSL connection is working, you can proceed with setting up OpenVPN.
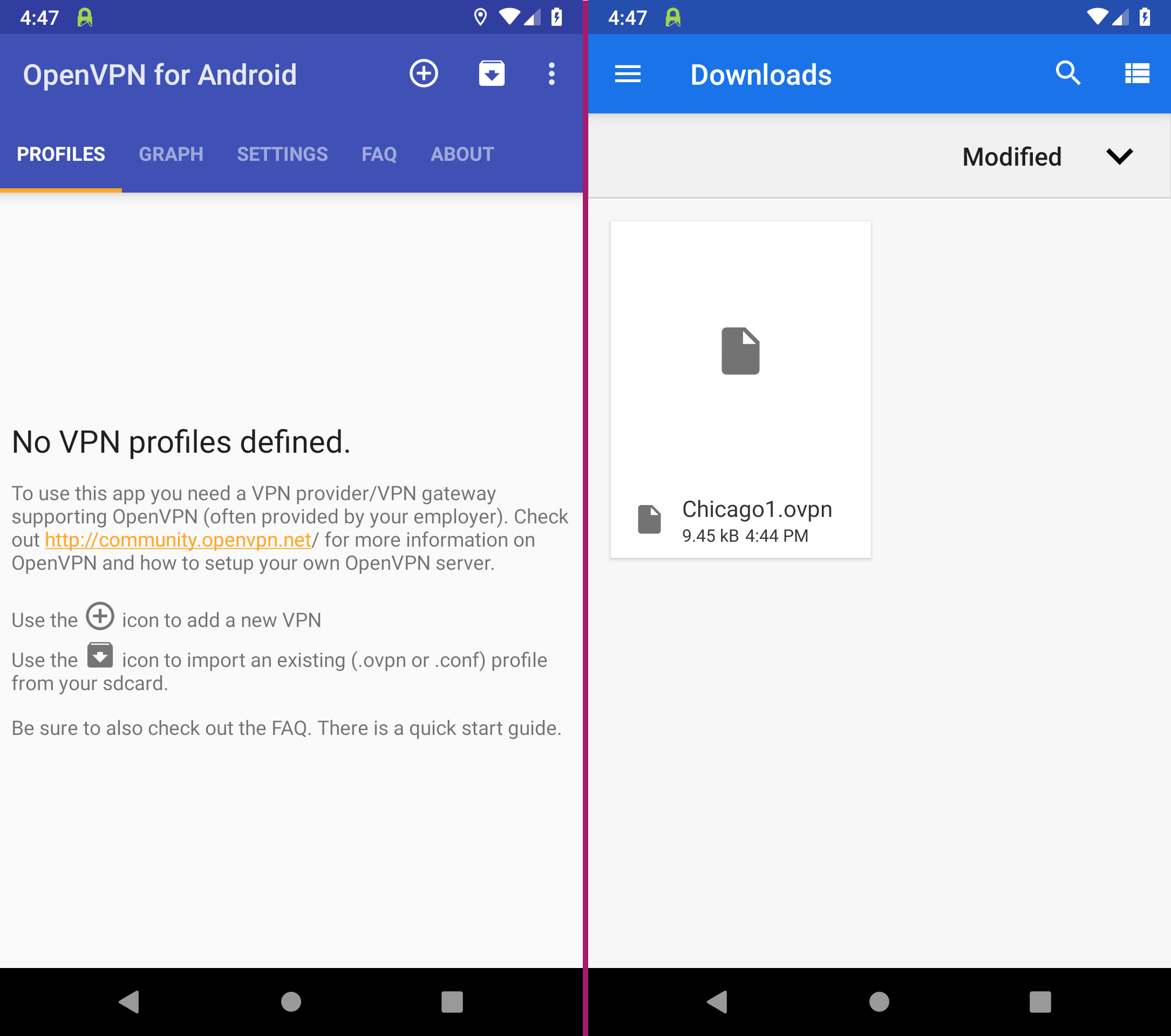
Open OpenVPN for Android and tap the import icon in the upper right corner (package with arrow pointing down).
In the Downloads folder, open the .ovpn file you just downloaded.
If you can't find the downloads folder immediately, you can also access it via the Burger menu at the top left (three dashes).
Establish the OpenVPN connection
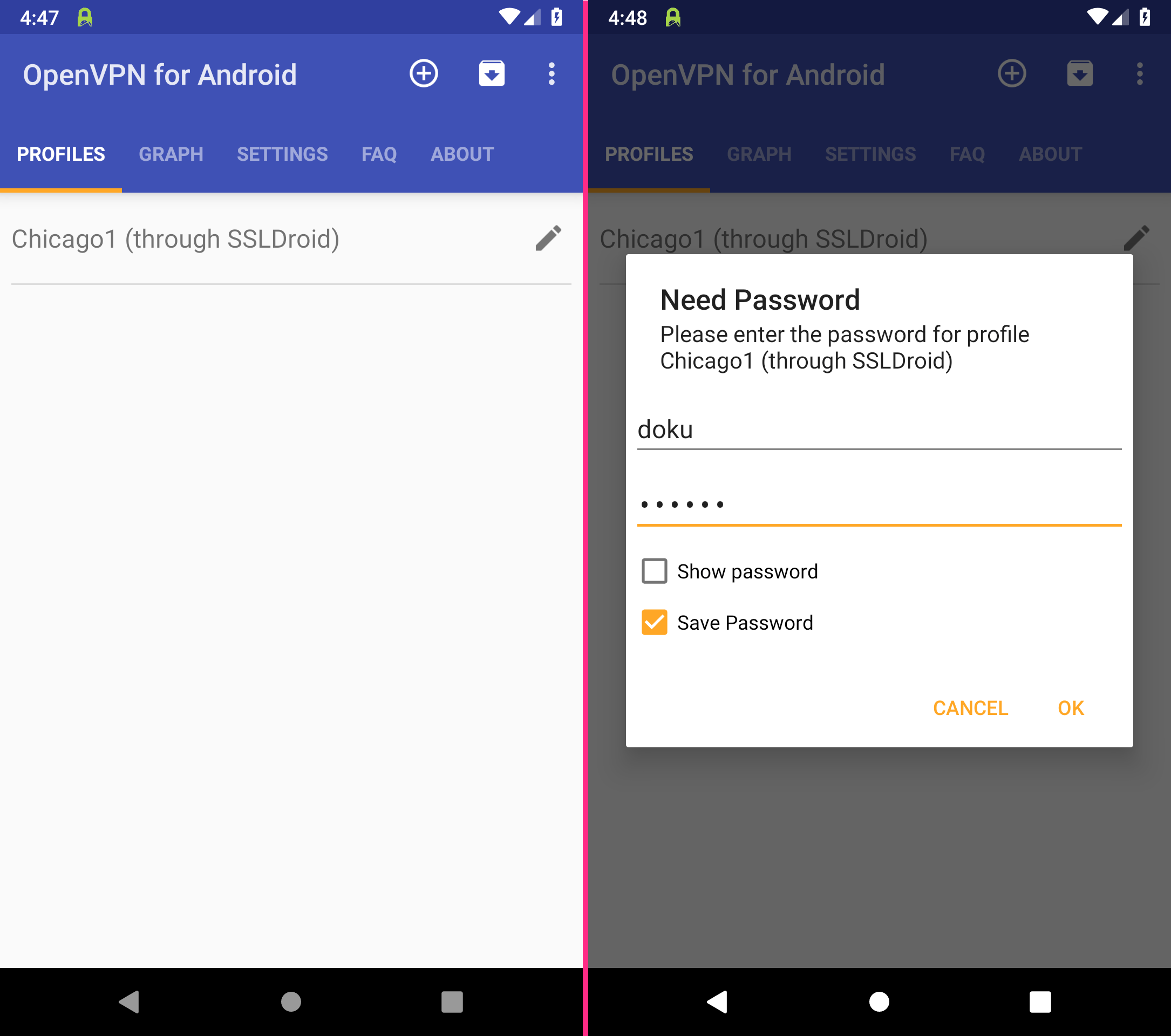
Tap the VPN profile you have just set up to establish a connection.
The first time you establish a VPN connection with OpenVPN for Android, you must first confirm by clicking OK.
Then enter your credentials for Perfect Privacy and tick Save Password.
Confirm the password dialog with OK.
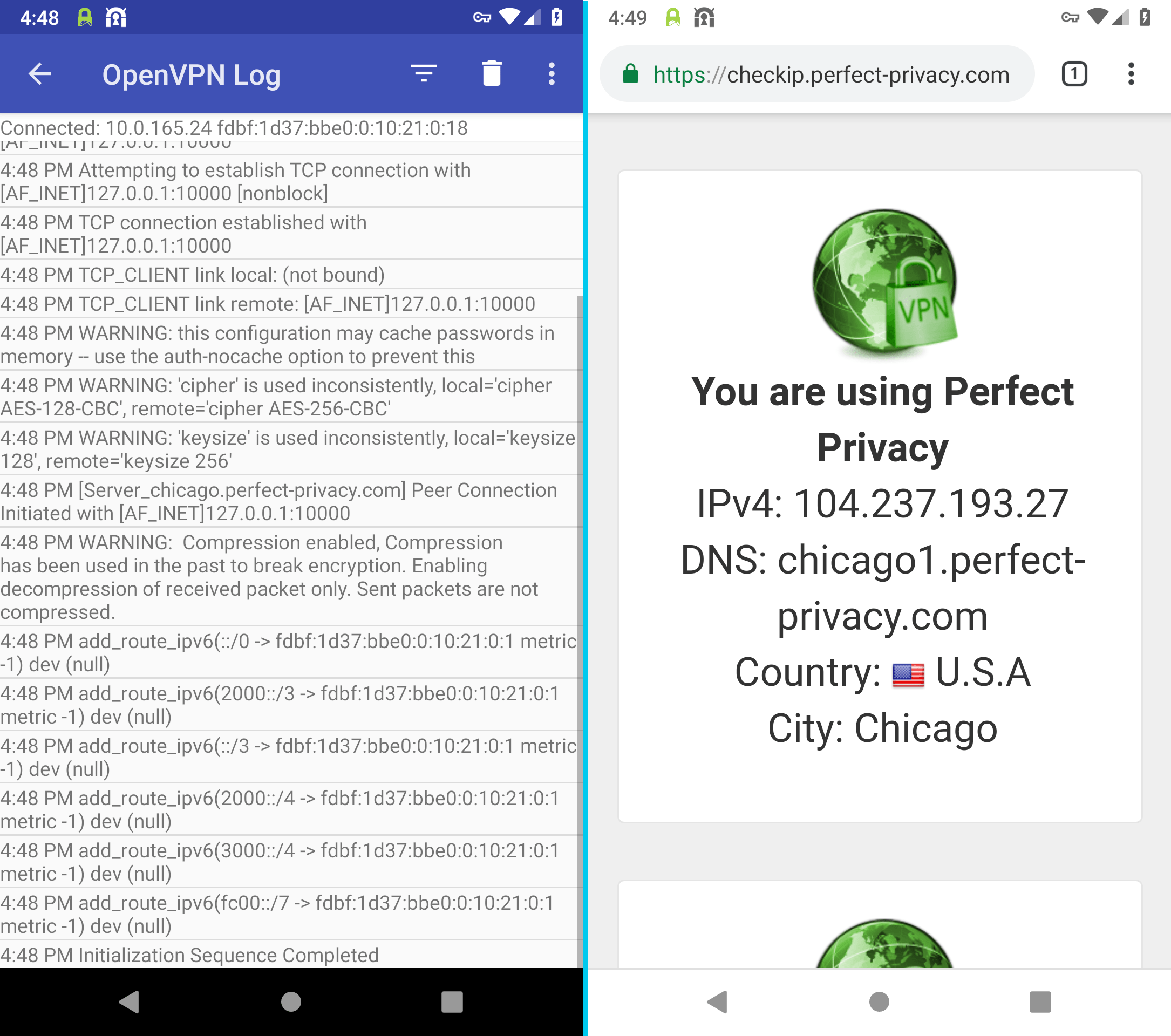
After a short moment the OpenVPN connection is established. At the bottom of the protocol view it says Initialization Sequence Completed.
The OpenVPN for Android icon at the top of the system bar indicates that the VPN connection has been established - even when the app is closed.
You can now verify that the VPN connection is working correctly by going to our Check-IP page.
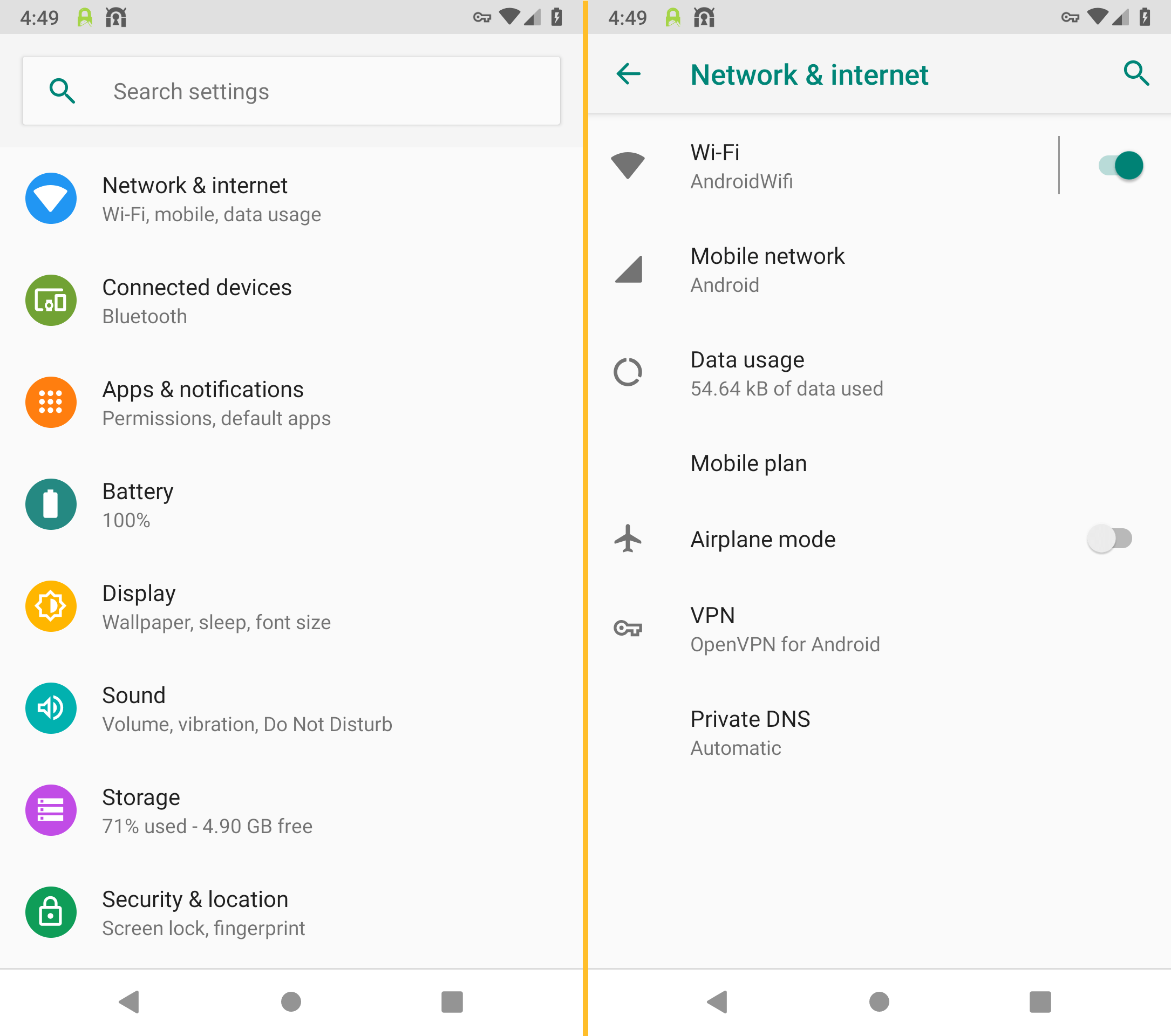
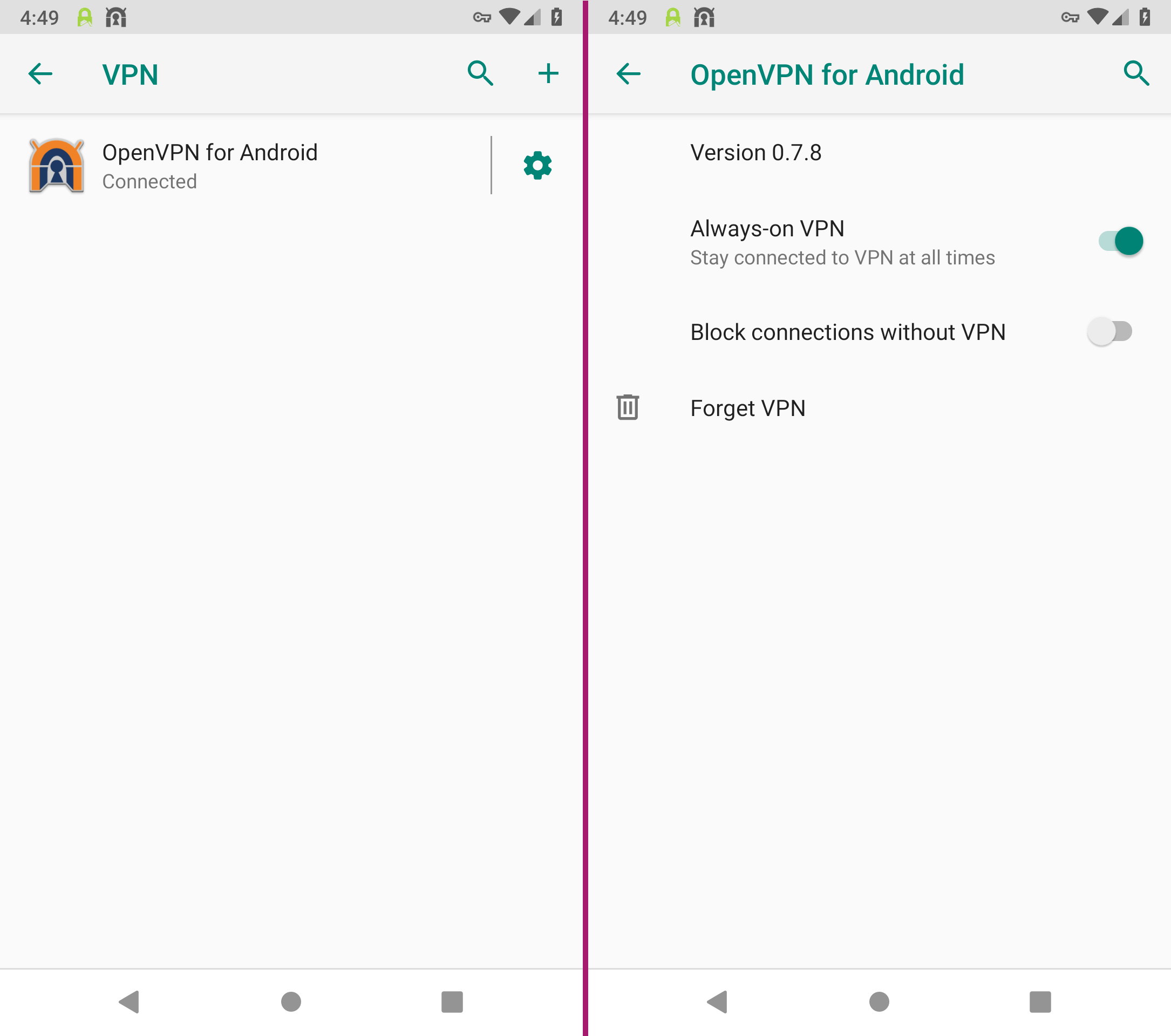
Tap on the gear next to OpenVPN for Android.
Now turn on the option Always-on VPN.
Please note: The option Block connections without VPN must remain disabled, because the SSL connection by SSLDroid must not be blocked.
Compatibility: Unfortunately, these options are not available on Huawei and Honor devices (EMUI interface) (as of Android 9.0).


Questions?
If you have any questions, comments or other feedback regarding this tutorial, please use the corresponding thread in our community forums.